Not Replaced — Rewired: How Recruiters Thrive with AI
Introduction: The Rewired Reality of Recruitment Let’s be honest—every recruiter has heard the same line lately: “AI is coming for…
2025 is not ending in a whimper; it’s ending in a wake-up call. The year’s defining breaches—crippling ransomware, months-long dwell times, and the agonizing $4.44 million average cost—were not caused by zero-day threats. They were caused by systemic complacency, poor governance, and the failure to break old, bad habits.
As we close out 2025, the truth is clear: the digital landscape didn’t fail due to technology; it failed due to a lack of fundamental organizational resilience. For years, cybersecurity was treated as a siloed IT cost center. In 2025, that approach became obsolete. We are now in an era where every unverified access or delayed patch quickly escalates to a board-level crisis.
Your security posture is now an explicit measure of your financial stability. If your organization is merely playing defense, you are at risk of a severe 2026 meltdown. This deep dive outlines the diagnosis of 2025’s critical failures and presents the three essential, actionable fixes required to shift your cyber strategy services from simple prevention to resilient foresight.
The crises of 2025 boiled down to five repeating organizational failure loops. Our analysis confirms that the following three loops are the most high-impact and high-frequency, requiring immediate, critical attention before January 1st.
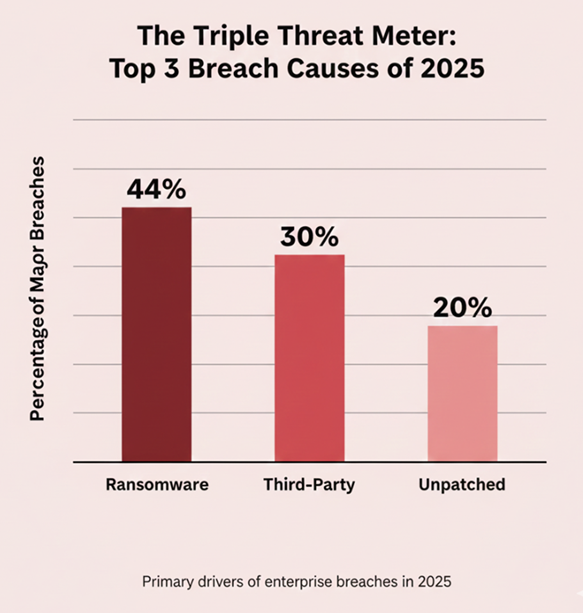
The supply chain has become the single largest unregulated perimeter. 30% of 2025 breaches originated with a third-party vendor compromise. The core failure is not the vendor’s weak security, but the client’s lack of visibility, which permits excessive cloud permissions and inactive API tokens. Attackers simply follow the “Chain of Trust”—the path of over-granted access—to your critical data store. They are walking through your partners’ gates, not yours. Organizations require robust cybersecurity services focused on supply chain risk, but most are still playing catch-up.
Identity Drift is the engine of nearly all lateral movement. User accounts accumulate unnecessary permissions (Privilege Creep), giving attackers a clear roadmap for escalation once a credential is stolen (often via AI-driven phishing). The failure here is not the difficulty of the theft, but the ease of the subsequent takeover. Enterprises are failing to implement modern identity and access management solutions that enforce the principle of least privilege, allowing basic credential theft to turn into a full corporate takeover.
Enterprises are consistently losing the race against exploit development. Nearly 20% of successful breaches this year exploited known, unpatched KEVs (Known Exploited Vulnerabilities) on critical edge devices. Attackers are highly efficient: they use threat intelligence services to systematically monitor CISA’s catalog and move in days. An enterprise patch cycle that takes weeks or months is no match for an attacker moving right now. This disconnect between known risk and delayed fix is a monumental organizational failure.
The path to overcoming these persistent failures is a shift in focus from simply preventing every attack (an impossible goal) to becoming an organization that can anticipate, absorb, and recover from attacks faster than the global 241-day average.
Compunnel’s analysis points to three critical strategic actions—rooted in our Four Pillars of Enterprise Resilience—that must be the foundation of your 2026 security budget.
The Mandate: Turn Intelligence into Actionable Policy.
The first fix is the shift from reactive, alert-driven defense to a predictive model. This is where advanced cybersecurity solutions and threat intelligence services dictate action before the attacker moves.
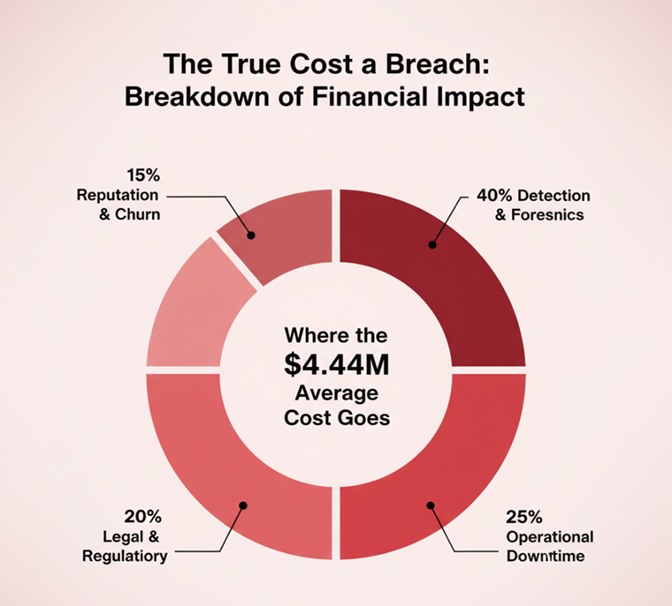
The Mandate: Eliminate Identity Drift and Seal the Third-Party Gates.
The perimeter is obsolete. Effective cyber security services must enforce a non-negotiable Zero-Trust Architecture (ZTA), protecting the data itself, not just the network edge.
The Mandate: Test Your Recovery Plan Before the Crisis Hits.
The ultimate measure of resilience is the speed and reliability of your recovery. 2025 data proved that companies with tested response plans save an average of $1.49 million per breach.
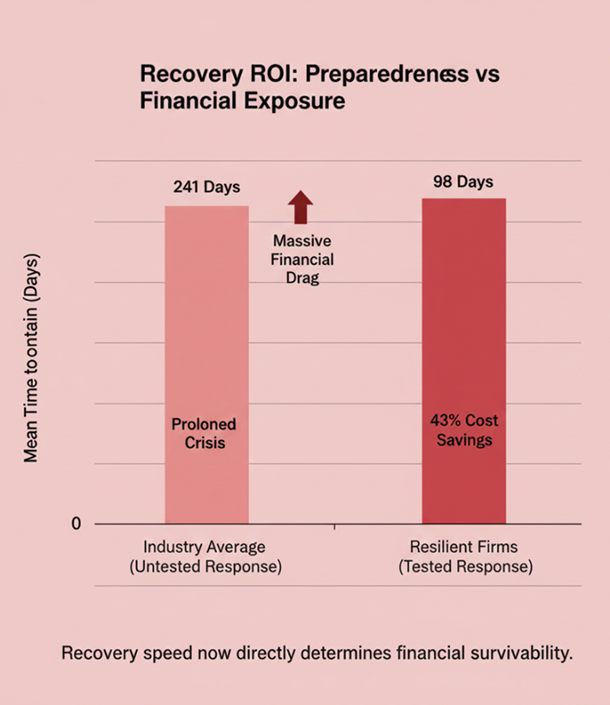
2025 is proving to be the year of unmasking. It revealed that the biggest threats are not complex new malware, but systemic failures in adopting basic best practices.
The horizon ahead is defined not by fear, but by intelligence and purpose. The organizations that will define 2026 are those that anticipate and absorb risk. To achieve true digital resilience, enterprises need integrated, strategic cybersecurity services that elevate foresight to the level of infrastructure.
Don’t let the same mistakes define your 2026.
Download the full report, Cybersecurity Lapses 2025: What Broke, Why, and Fixes, to partner with a trusted cybersecurity services provider and build the resilient strategy that will save your organization in the year ahead.
