Contingent Workforce Solutions in 2026: How Enterprises Are Building Agile Talent Models
As we enter January 2026, the traditional corporate "headcount plan" is undergoing a quiet but radical retirement. For decades, the…
The phrase “Zero Trust” has become the security industry’s most comfortable lie. It was a philosophy of necessary skepticism—never trust, always verify—that promised to decouple security from the network boundary. Today, it has metastasized into an operational morass of tool sprawl, static policy engines, and siloed identity solutions that simply cannot keep pace with the velocity of business transformation. For the CISO, CIO, and the Board, the blunt truth is this: Zero Trust, as implemented by most global enterprises, is operationally collapsing. The foundation of modern security is not a single control framework; it is the uncomfortable and continuous recognition of inherent, measurable exposure.
Zero Trust was a powerful corrective to the archaic trust models of the 2000s. It worked precisely because it placed identity and device posture at the center, finally forcing enterprises to authenticate users accessing the corporate LAN. However, that design relied on a relatively controlled, corporate-owned environment. In 2025, that environment will be extinct. We have reached a point where dynamic threats, shadow AI adoption, and the sheer volume of machine identities—now outnumbering human identities by an estimated 40:1—have rendered static, policy-driven trust decisions inert. The operational reality is not “zero trust,” but “too much to trust,” leading to a state of perpetual alert fatigue and unprioritized risk.
The conceptual perimeter died years ago, but the perimeter mindset lingers, suffocating modern security programs. The culprits are not singular, but systemic: the proliferation of multi-cloud architectures, the exponential growth of third-party SaaS integrations, and the API-driven economy. Every microservice is a potential front door. Every partner integration is an unmanaged guest. Remote work pushed the control plane to employee homes, and now, the rapid and ungoverned deployment of AI models within business units has introduced a novel category of “Shadow AI” exposure—data is being consumed and processed in environments the security team doesn’t even know exist.
Network boundaries, firewalls, and VPNs are now little more than historical artifacts that give a false sense of security while the true attack surface explodes. This is precisely why modern enterprises are shifting toward unified exposure visibility across cloud, identity, and data—the same convergence Compunnel addresses through its Cybersecurity Services & Risk Transformation Solutions practice.
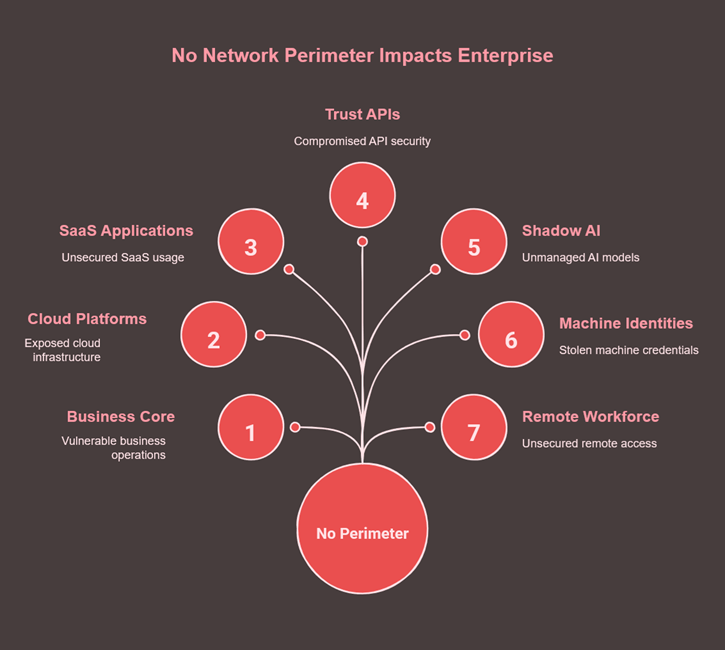
This new reality forces a paradigm shift from a prevention-centric mindset to an assumption-of-continuous-exposure operating model. This is the definition of Continuous Exposure Management (CEM). CEM is not simply a new name for vulnerability scanning or the next iteration of Zero Trust. It is a live, always-on strategy that shifts the focus from managing security controls to actively managing the true financial risk of exposure. It accepts that breach is not a possibility, but a certainty—and the CISO’s role is to minimize dwell time and business impact.
CEM necessitates a fundamental transformation in how risk is assessed. The old model centered on managing assets and vulnerabilities; the new model is focused entirely on threat-path validation and business context.
| Legacy Security Model | Continuous Exposure Management |
| Static policies & control checks | Live attack surface intelligence |
| Technical severity (CVSS) | Financial impact (Risk-in-Dollars / EML) |
| Prevention-centric mindset | Assumption of continuous exposure |
| Periodic assessments | Real-time validation & remediation |

In 2026, “continuous” will not mean faster scans—it will mean persistent enterprise-wide exposure awareness:
This is where security becomes live enterprise risk intelligence, not a reporting function.
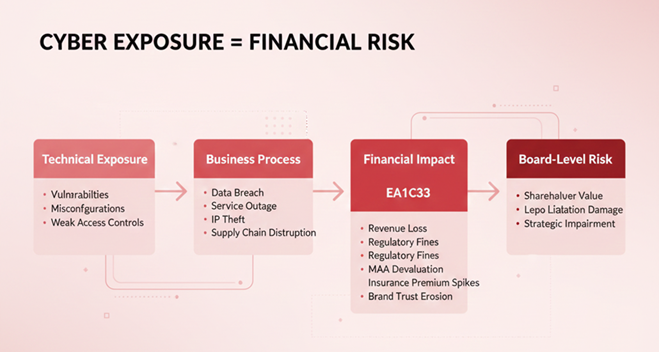
This shift has profound business consequences that leadership can no longer defer. Exposure is no longer a technical metric; it is a financial one. Unmanaged exposure directly impacts:
The cyber insurance market has already hardened. Insurers now demand continuous, auditable evidence of risk reduction, not static questionnaires.
A 2024 IBM study—Cost of a Data Breach Report—found that the global average cost of a breach has reached $4.45 million, a 15% increase in just three years, underscoring the accelerating financial gravity of unmanaged exposure.
Boards no longer need RAG charts. They need Estimated Maximum Loss (EML) mapped to critical business processes in real time.
The security operating model for 2026 must be exposure-first, not control-first. Risk prioritization must drive tool orchestration—not the reverse.
This model requires:
This is the same convergence of identity, cloud, and data risk that Compunnel enables through its Identity, Cloud & Data Security Alignment Framework.
Most enterprises, however, are poised to fail this transition. The patterns are predictable:
Navigating this structural transformation requires a partner that operates with the mindset of a Chief Risk Officer—not a product reseller. Compunnel sits precisely at this intersection of technology, governance, and business risk.
We enable the strategic shift to an exposure-centric security model by delivering:
This is not a security control deployment. This is security as measurable business assurance—the same governance-driven model advanced through Compunnel’s Enterprise Risk & Compliance Security Programs.
By 2026, attackers won’t waste their time battering firewalls or chasing weak passwords. Their focus has already shifted to the connective tissue of the enterprise—APIs, machine identities, unmanaged SaaS, and Shadow AI supply chains. Perimeter-first security models are becoming structurally irrelevant. What will matter instead is an organization’s ability to see, quantify, and govern exposure continuously.
The most urgent priority for 2025 is not replacing tools. It is rebuilding the security program around a business-aligned risk model—one that expresses exposure in terms of revenue at risk, operational downtime, and regulatory liability, not technical severity. The question is no longer whether your organization is exposed. It is whether that exposure is invisible, unmanaged, and financially unquantified.
If your board asked today for a real-time, dollar-based view of cyber exposure across cloud, SaaS, identities, and AI systems, could you deliver it with confidence? If not, your security strategy is still anchored in an outdated perimeter mindset while adversaries have already moved on.
This is the moment to redesign security as a business risk engine—not an IT cost center. It begins with clarity: understanding where exposure truly lives, how it propagates, and what it costs your enterprise when left ungoverned.
To take that first step, download Compunnel’s latest report—State of Cybersecurity 2026: What Will Drive Risk & Spend—and gain a research-backed blueprint for building an exposure-first security program before the next wave of threats arrives.
Read Also: Is your organization truly secure? How to use AI to answer this question?
