Contingent Workforce Solutions in 2026: How Enterprises Are Building Agile Talent Models
As we enter January 2026, the traditional corporate "headcount plan" is undergoing a quiet but radical retirement. For decades, the…
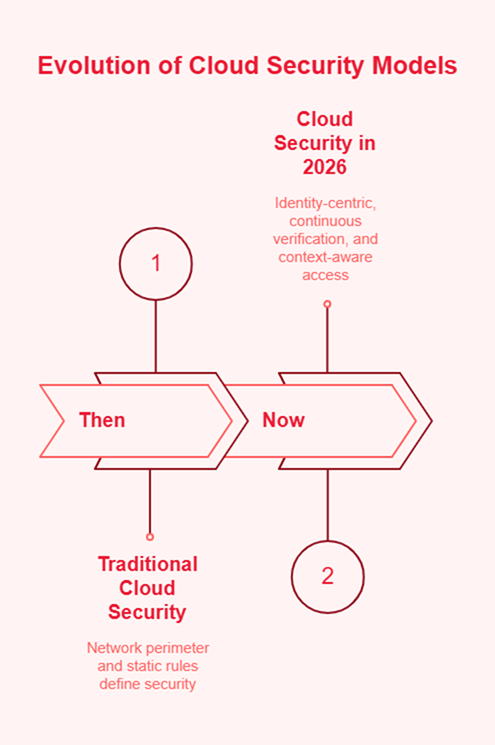
The friction you feel in your security operations isn’t a resource gap; it’s a structural collapse. For a decade, we built cloud security on the assumption that we could draw lines around assets. We treated the cloud like a faster, more ephemeral version of the data center.
By the start of 2026, that logic has officially failed. The “perimeter” isn’t just porous—it’s non-existent. In an ecosystem defined by ephemeral workloads, thousands of interconnected APIs, and autonomous AI agents, the traditional network-centric model has become a liability. We are no longer defending a fortress; we are managing a fluid, high-velocity state of constant access.
The collapse of the perimeter was not a single event, but a steady erosion caused by the reality of the modern enterprise. Your data no longer lives “in” the cloud; it flows across a mesh of multi-cloud environments, third-party SaaS, and edge deployments.
In this environment, the network is merely the plumbing. Attackers have long since stopped trying to “break in” through a firewall. Instead, they log in. They exploit over-privileged service accounts, dormant identities, and misconfigured API keys. When an AI agent moves data between a Snowflake instance and a custom LLM application, there is no “edge” to defend. The risk is not in the connection, but in the permission.
The most common leadership reflex to this instability is to buy more. But the “tooling-first” era has reached a point of diminishing returns.
Adding another dashboard to a SOC that is already drowning in 10,000 daily alerts doesn’t increase security—it increases noise. Most enterprises are now managing a fragmented graveyard of legacy agents and disconnected cloud-native security platforms. This fragmentation is where breaches live. When your security posture is a collection of silos, you lose the ability to see the “attack path”—the sequence of movements an adversary takes across identity, storage, and compute.
This is a failure of the operating model. You cannot solve a systemic visibility problem with a point solution.
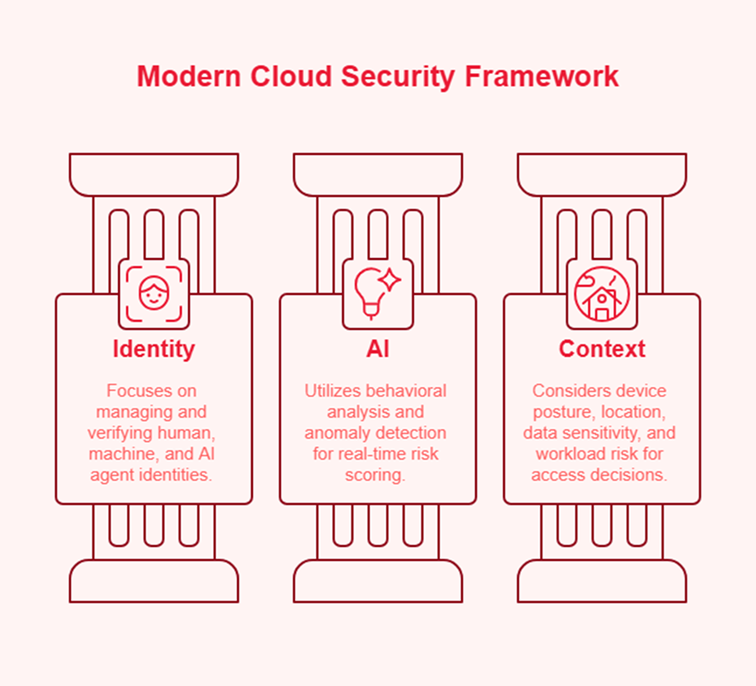
If the network is no longer the control plane, what is? In 2026, security leadership must pivot to a model where Identity, AI, and Context form the foundation of every decision.
To stay ahead, cloud security services must transition from “monitoring” to “intelligent orchestration.” We are moving away from static rules toward continuous, identity-aware enforcement.
Effective services in this era don’t just alert you to vulnerability; they understand the business risk. They integrate governance across the entire stack—from the code in your CI/CD pipeline to the data sitting in a vector database. The goal is an integrated ecosystem where security is an invisible layer of architecture, not a gated checkpoint that slows down the business.
This requires a shift toward outcomes: rather than measuring how many vulnerabilities were patched, boards should be looking at the reduction in “blast radius”—how much damage an attacker can do once they inevitably gain an initial foothold.
As we enter 2026, the questions coming from the C-suite and the Board must change.
Stop asking:
Start asking:
Strategy, not tooling, determines security outcomes. A leader’s job is to ensure that the organization’s architecture reflects the reality of the threat landscape, not the comfort of legacy habits.
2026 is the year we stop pretending the old controls work. The shift from perimeter defense to control intelligence is not an incremental update, it is a survival requirement.
As you finalize your plans for the new year, remember that the most dangerous thing an organization can do is apply 2016 ideas to 2026 problems. New ideas aren’t just about innovation; they are about alignment with the current reality of the cloud. The organizations that thrive will be those that stop buying tools and start building intelligence.
Ready to turn these ideas into an actionable roadmap for 2026? Start the year with a strategy that matches the scale of your ambition. Let’s look past the tools and focus on the architecture of your resilience.
Book your 1:1 Cloud Security Strategy Session with us today.
