You Do Not Need a Legal Entity to Own a Global Market. You Need This
The Incorporation Trap Has a Body Count It starts with ambition. A decision is made to enter a new market…
2025 is a defining year for enterprise security, but not in the way predicted. The breaches currently stealing headlines- the data leaks, the crippling ransomware, and the months of downtime- aren’t caused by exotic threats. They are the catastrophic result of unbroken old habits in governance and preparedness.
At Compunnel, our report, Cybersecurity Lapses 2025: What Broke, Why, and Fixes, delivers one stark conclusion: the global digital landscape isn’t failing due to a lack of technology; it is failing due to a lack of fundamental organizational resilience.
For years, cybersecurity was a siloed, tactical cost center. In 2025, that approach became obsolete. We are now immersed in an era where every third-party connection or delayed patch escalates quickly into a systemic, board-level crisis.
This deep dive examines the five major failure loops defining the year, unmasking the critical disconnect between enterprise spending and actual resilience, and outlining the modern cybersecurity solutions required to fix them as we close out the year.
The surging financial impact of 2025 breaches is finally moving cybersecurity from the server room to the boardroom. Costs are swelling dramatically, driven by fines, lost business, and protracted recovery.
The surge isn’t primarily from nation-state actors, but from two connected vectors:
These statistics underscore the vital shift: an organization’s security posture is now an explicit measure of its financial stability and overall business resilience.
Compunnel’s analysis identifies five repeating organizational failure loops that, despite all the spending on next-gen tech, are persisting across nearly 80% of major incidents reported this year.
The supply chain is proving to be the single largest unregulated perimeter. With over 30% of breaches traced back to a third-party vendor compromise, many organizations have little to no visibility into the cloud permissions or inactive API tokens granted to their external partners. A single compromise in a small, peripheral SaaS provider often provides a direct, high privilege backdoor into a Fortune 500 client’s network.
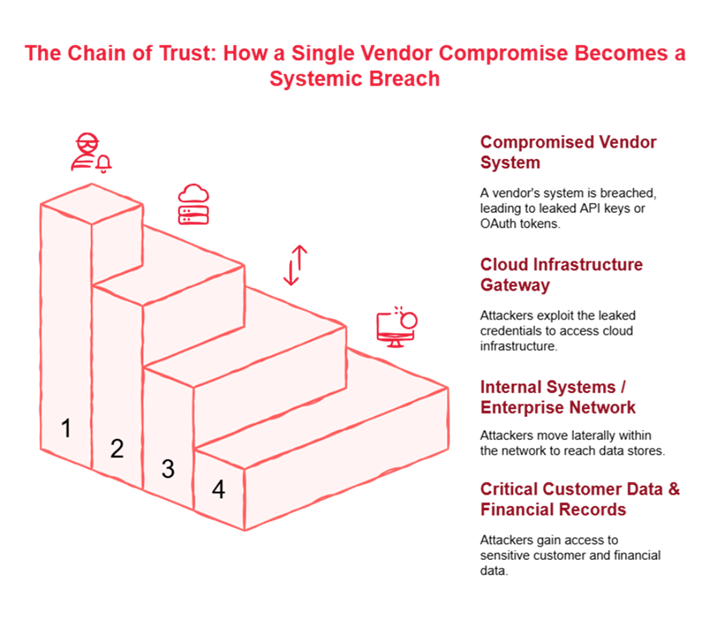
Attackers continue to win the patching race. Nearly 20% of successful breaches exploit known, unpatched vulnerabilities—often on critical edge devices like VPN gateways. Attackers leverage threat intelligence services to monitor KEVs (Known Exploited Vulnerabilities) and move faster than enterprise patch cycles. This time gap is a monumental organizational failure.
This loop is the engine of lateral movement. Over time, accounts accumulate unnecessary permissions, leading to Identity Drift. When a credential is stolen, this over-privileged account allows the attacker to escalate privileges and move freely. Organizations are failing to properly implement identity and access management solutions, allowing basic credential theft to turn into a full corporate takeover.
GenAI has significantly lowered the barrier for customized social engineering. The human element, accounting for 60% of all breaches, remains the easiest, uncatchable vulnerability, as AI-crafted lures bypass standard security filters and training.
Many enterprises have an Incident Response (IR) Plan—it just isn’t tested. When an attack hits, teams struggle with manual triage and poor containment protocols, leading to an extended breach lifecycle. Companies that conduct regular IR plan testing save an average of $1.49 million per breach —a clear financial incentive to move past paper-based planning.
The path to resilience requires shifting focus from simply preventing every attack to rapidly anticipating, absorbing, and recovering from inevitable breaches. This strategic pivot is best facilitated by an experienced cybersecurity services provider.
Compunnel recommends adopting the Four Pillars of Enterprise Resilience:
True resilience starts with anticipation. Use automated, AI-driven threat intelligence services and behavioral analytics to anticipate attacker intent before impact. Moving from “alert fatigue” to predictive foresight slashes Mean Time To Detect (MTTD) by up to 55%.
The perimeter is dead. Effective cybersecurity solutions must protect the data itself. Rigorously apply Zero-Trust Architectures (ZTA) and invest in advanced Identity Threat Detection and Response (ITDR). By focusing on core defense, enterprises build segmented protection against lateral movement.
This breaks organizational habits. Cybersecurity must align with ESG and core business risk frameworks. A cybersecurity services provider can offer virtual CISO services to embed compliance and risk management into daily operations. This alignment, backed by data protection services, improves compliance readiness by over 38%.
The ability to recover quickly is the ultimate measure of resilience. Establish Immutable Backup Architectures and implement pre-tested Crisis Communication Frameworks. A robust cyber strategy services model includes regular, realistic tabletop exercises, aiming for full recovery in under 100 days—dramatically outperforming the global 241-day average
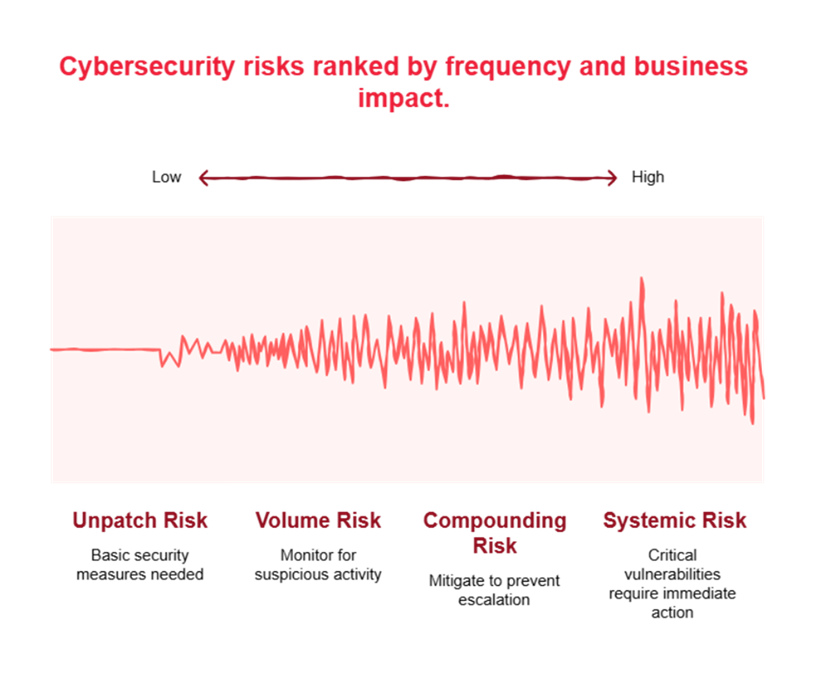
2025 is proving to be the year of unmasking. It has been revealed that the biggest threats aren’t the complex new malware strains, but the systemic failures to adopt simple best practices in a complex multi-cloud world.
The horizon ahead is not defined by fear; it is illuminated by intelligence, collaboration, and purpose. The organizations that will define 2026 and beyond are not those that avoid risk, but those that anticipate and absorb it. The time for treating security as a checkbox exercise is over. To achieve true digital resilience, enterprises need integrated, strategic cybersecurity services that elevate foresight to the level of infrastructure.
Download the full report, Cybersecurity Lapses 2025: What Broke, Why, and Fixes, for comprehensive data, strategic frameworks, and actionable steps your organization can take right now to secure its future.
