Cloud Security in 2026: Why Identity, AI, and Context Will Replace Traditional Controls
Introduction The friction you feel in your security operations isn't a resource gap; it’s a structural collapse. For a decade,…
The final report was bound, the CISO’s signature was dry, and the board-level dashboard glowed with a comforting, uniform green. By all traditional metrics, the annual audit was a triumph. The enterprise had successfully demonstrated its adherence to every requisite framework, checking off a thousand microscopic boxes across identity, encryption, and data residency.
Six months later, the breach investigation begins.
The forensic team discovers that the initial point of entry was a misconfigured cloud storage bucket—one that had been perfectly compliant during the audit but was “drifted” into an insecure state by a routine DevOps update just forty-eight hours after the auditors left. This is the quiet crisis facing regulated industries in 2026: we are passing our audits, but we are failing to manage our risk. In this high-velocity environment, traditional cybersecurity compliance services must evolve or risk becoming a legally sanctioned theatre.
We are witnessing a structural mismatch between the speed of regulation and the speed of reality. Enterprises are spending more on compliance than ever before, yet the sense of certainty is at an all-time low.
This is not a failure of effort, but a failure of timing. Compliance, in its legacy form, operates in snapshots—quarterly reviews or annual “point-in-time” certifications. Risk, however, operates continuously. According to the Verizon 2024 Data Breach Investigations Report (DBIR), the exploitation of vulnerabilities as a breach vector increased by 180% in a single year, largely driven by zero-day threats that materialize in hours, not months.
Furthermore, the IBM Cost of a Data Breach Report 2024 indicates that the average time to identify a breach is still 194 days. If your compliance cycle is 365 days, an attacker could live in your environment for two full quarters while you continue to present “compliant” reports to your board.
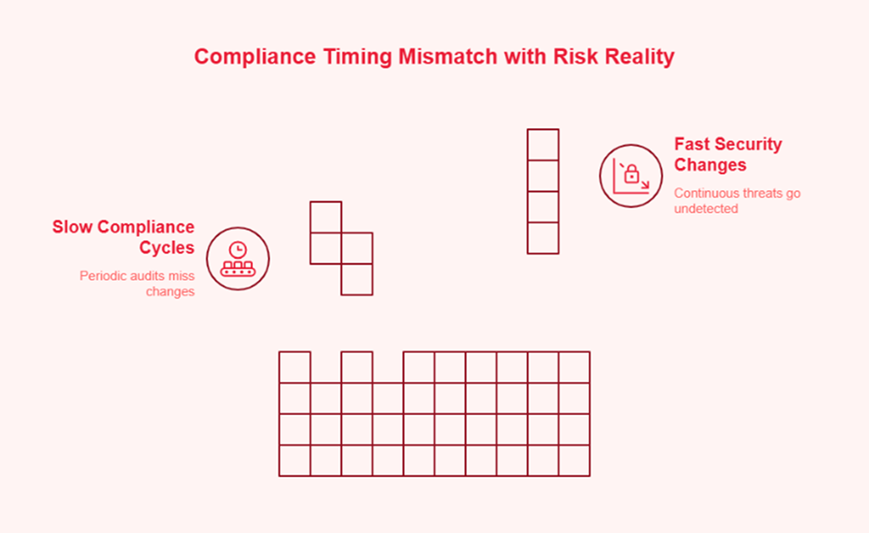
The “checklist era” was designed for an age of static infrastructure—servers that lived for years and software that updated twice a decade. In 2026, the shift to serverless architectures, ephemeral containers, and autonomous AI agents has destroyed the concept of a “static truth.”
Evidence now decays the moment it is collected. A screenshot of a firewall rule taken on a Tuesday is worthless by Wednesday if a CI/CD pipeline has redeployed the entire network stack. We must accept a hard truth: Compliance is no longer a document; it is a telemetry problem. Continuous assurance is the only survivable response. It moves the burden of proof from manual human collection to automated system validation. It recognizes that in a world of 10,000 daily configuration changes, a human-led audit is nothing more than a historical artifact.
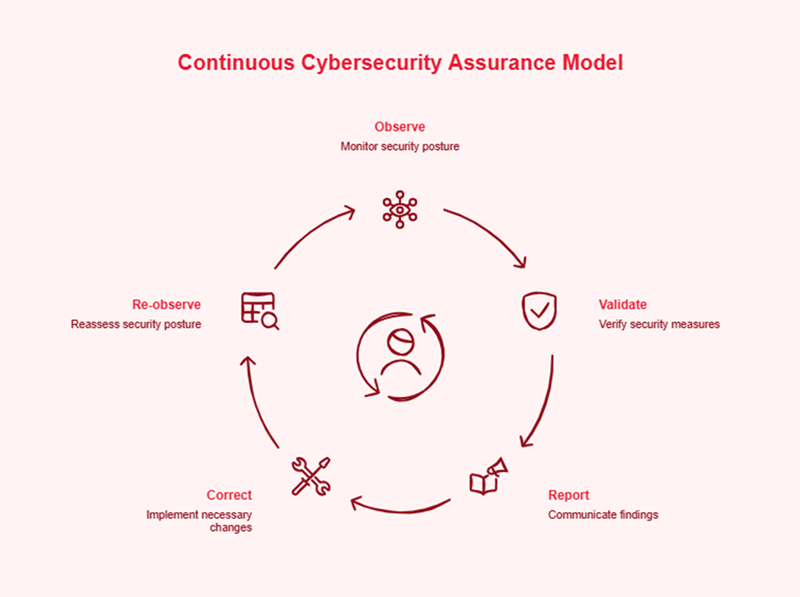
In this new landscape, cybersecurity compliance services are being redefined as the bridge between raw security telemetry and executive governance. It is no longer enough for a service provider to help you “get ready” for an audit; they must provide the infrastructure to ensure you never leave a state of readiness.
Modern cybersecurity compliance services in 2026 must provide:
By shifting to these intelligent cybersecurity compliance services, organizations can transform compliance from a reactive cost center into a managed security advantage that protects the brand’s integrity as much as its data.
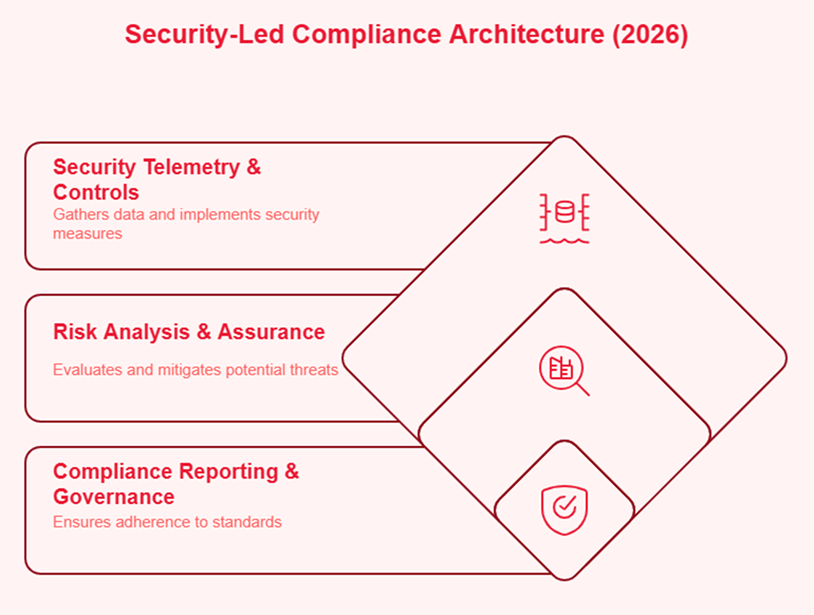
As we move through 2026, the expectations of the boardroom and the regulator are converging. Regulators are beginning to ask for “living evidence”—API-driven feeds that prove control health—rather than static PDF reports.
Boards of Directors are also shifting their line of questioning. They are no longer satisfied with a “Pass/Fail” binary. They want to know the “Mean Time to Compliance”—how long the organization remains in a non-compliant state after a change occurs. Security and compliance teams will increasingly be judged not on the absence of audit findings, but on the speed of their threat intelligence and response when a control fails.
Compliance didn’t get harder; reality simply got faster. The enterprises that continue to rely on manual, snapshot-based audits will find themselves perpetually behind the curve, holding “green” certificates that offer no protection against modern threats.
In 2026, assurance is no longer something you prove once a year. It is something you maintain every second. Transitioning your cybersecurity compliance services to a continuous model is not just a regulatory strategy—it is the only way to ensure that your “green” dashboard actually means you are safe.
Is your compliance posture a reflection of today’s reality or last year’s audit? Let’s discuss how to move your organization toward a model of continuous assurance and automated governance.
Request a 1:1 Compliance Strategy Session to assess your regulatory readiness.
