Contingent Workforce Solutions in 2026: How Enterprises Are Building Agile Talent Models
As we enter January 2026, the traditional corporate "headcount plan" is undergoing a quiet but radical retirement. For decades, the…
If you walked into your Security Operations Center today and felt a palpable sense of exhaustion, it isn’t because your team lacks talent. It’s because they are fighting a war of attrition against operational math that they cannot win.
For years, we have scaled our SOCs by adding more heads and more tools, assuming that more “eyes on glass” would eventually bridge the detection gap. But as we enter 2026, that model has hit a hard ceiling. The volume of telemetry from cloud-native environments, ephemeral workloads, and distributed identities has far outpaced human cognitive limits. In this environment, traditional security operations services that rely on manual triage are no longer just inefficient—they are a structural risk to the enterprise.
The legacy SOC model is built on a “linear triage” philosophy: when an alert fires, a Tier 1 analyst reviews it and either dismisses or escalates it. This worked when we were managing firewalls and static servers. It fails in a world where an attack can move from initial access to full domain dominance in less than 90 minutes.
The reality is that detection is now faster than human response. According to the IBM X-Force Threat Intelligence Report 2024, the time attackers need to execute ransomware has decreased by 94% over the past several years. Furthermore, the 2024 CrowdStrike Global Threat Report highlights that the average “breakout time”—the window for an adversary to move laterally—has plummeted to just 62 minutes.
Despite these shrinking windows, the Google Cloud CISO Forecast and subsequent industry data consistently show that SOC analysts are still spending over 30% of their day on low-value manual tasks or investigating false positives. We are effectively paying our most expensive talent to ignore 70% of the alerts they receive because they simply don’t have the “bandwidth” to investigate them.
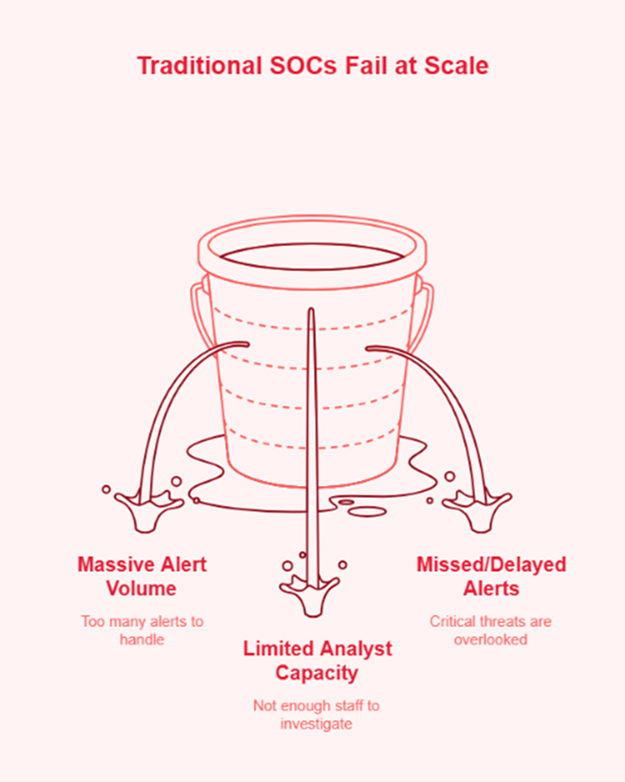
Moving to an AI-driven SOC isn’t about chasing a trend; it’s about reclaiming the time-to-respond. We have reached the point where humans cannot manually correlate signals across identity, endpoint, and cloud logs at the speed required to stop a modern breach.
AI in the 2026 SOC isn’t a “replacement” for the analyst; it is the filter that makes the analyst effective. AI-driven systems excel at pattern recognition and “noisy” signal correlation—identifying that a failed login in Tokyo, a new API key creation in AWS, and a strange outbound data flow are actually the same incident.
By the time a human analyst sees an incident in an AI-driven SOC, the “detect and correlate” work is already done. The analyst isn’t asking if something happened; they are deciding how to respond. This shift from “searcher” to “decider” is the only way to get Mean Time to Respond (MTTR) down from hours to minutes.
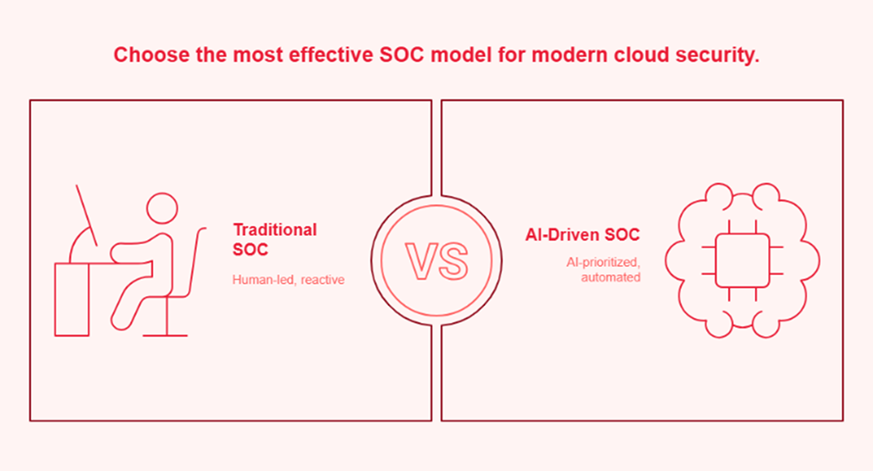
As you evaluate your internal capabilities or external partners, you must look for security operations services that have moved beyond the “monitor and notify” loop. In 2026, an effective security operations service must be built on three pillars:
This evolution allows your team to move away from tool management and toward true threat intelligence and hunting, focusing on the sophisticated adversaries that AI identifies but only a human strategist can fully neutralize.
As you sit in your 2026 budget reviews, the most dangerous thing you can do is maintain the status quo. If your “Security Operations” strategy is still measured by how many analysts you have per 1,000 endpoints, you are measuring the wrong thing.
Stop asking: “How many alerts did we see this month?” and “What is our headcount gap?”
Start asking: “What is our automated containment time?” and “How much of our managed security spend is going toward manual triage versus high-value engineering?”
The SOC of 2026 is an engineering problem, not a staffing problem. Resilience is determined by how well you can automate the mundane to liberate the expert.
The era of the “human-only” SOC is over, buried under the sheer weight of cloud-scale data. 2026 is the year that AI-driven security operations services become the baseline for any organization that intends to remain resilient against automated, machine-speed threats. Standing still isn’t a neutral choice; it’s a decision to let your response times drift further behind the attack curve.
The question isn’t whether your SOC will change, but whether you will lead that change or be forced into it by a post-incident review.
Is your SOC ready for the velocity of 2026? If you are concerned about analyst burnout, rising alert volumes, or response gaps, let’s have a grounded conversation about your current operational state.
Explore an AI-augmented security operations strategy and assess your SOC readiness here.
