Too Many Passwords, Too Little Security: What IAM Can Actually Solve
A Password Problem That Isn’t Really About Passwords In 2025, the average employee manages more than 150 passwords, and still,…
For most of the last decade, “Zero Trust” (ZT) was pitched as a guiding principle – aspirational, inspiring, yet often fuzzy. In 2025, that changed. Zero Trust stopped being a slogan and became a scoreboard. Boards and regulators no longer accepted glossy frameworks; they demanded proof that ZT delivered balance-sheet impact: reduced breach costs, faster recovery times, tighter identity control, and fewer crown-jewel systems at risk.
The pressure came from all sides. Global breach costs averaged $4.45M (and $10.22 in the U.S.), with multi-environment incidents ballooning into the costliest class. At the same time, the SEC’s four-day disclosure clock and the EU’s AI Act and NIS2 directives forced directors to treat ZT not just as an IT project, but as a fiduciary obligation. In that context, “Zero Trust maturity” stopped being about checklists and started being about proof – metrics boards could put next to financial KPIs.
So, did Zero Trust deliver or disappoint in 2025? The short answer: both. It delivered where organizations treated it as architecture – identity-first access, microsegmentation, policy-as-code, and automated isolation with outcomes they could measure. It was disappointing when it was reduced to a VPN replacement or another line item in the tool stack. This blog takes stock of both sides and lays out what it takes to make ZT a true performance engine in 2026.
NIST’s reference defines Zero Trust as a set of paradigms that move defenses from static perimeters to continuous, identity- and context-driven authorization for users, devices, applications, and data. The U.S. public sector sharpened expectations with the CISA Zero Trust Maturity Model (ZTMM) and sector strategies (e.g., DoD’s ZT roadmap), framing measurable progress across identity, device, network/segmentation, application, and data pillars.
In 2025, federal momentum continued: the DoD issued a new directive-type memorandum to align resources with its ZT strategy through 2026 – a signal that large, complex enterprises can effectively anchor ZT in governance, funding, and milestones.
Yet even with frameworks, ZT is tough. It demands identity cleanup, data labeling, policy-as-code, segmented networks, and operational muscle to prove controls in live drills. That’s why the year’s story is split between wins (identity-first access, reduced lateral movement, faster containment) and friction (workarounds, tool sprawl, and inconsistent enforcement).
Verdict so far: ZT delivered where identity and segmentation were engineered end-to-end and measured; it disappointed where ZTNA-as-a-VPN or policy theater substituted for architecture.
1) Identity-First Access Reduced Attack Paths
Organizations that replaced shared credentials and standing VPN tunnels with phishing-resistant MFA, device posture checks, and per-request authorization saw fewer credential-stuffing escalations and cleaner incident containment. Google’s BeyondCorp model continued to provide a reference for least-privilege, context-aware access without traditional VPN dependency.
What made it work: consolidated identity stores, lifecycle automation for human and non-human identities (service principals, tokens), and policy engines that evaluate user × device × resource × risk on every request.
2) Segmentation Contained Lateral Movement
Microsegmentation (host- or workload-level) limited blast radius when an attacker got a foothold, converting potential enterprise-wide incidents into bounded, investigable scopes. This aligns with the CISA ZTMM network and data pillars and has become a core board-level story: fewer crown-jewel systems in scope, resulting in fewer days of disruption.
3) Policy-as-Code Made Compliance Actionable
Teams that encoded authorization and data-handling rules (e.g., OPA/Rego policies, ABAC) into pipelines produced evidence-ready controls for audits and disclosures – especially important under the SEC’s four-business-day incident disclosure rule and the expanding expectations for AI governance. These pipelines cut advisory costs, accelerated reporting, and provided boards with assurance that compliance wasn’t just paperwork, but live, testable safeguards. And with NIS2, liability for supplier oversight now sits squarely with directors, making Zero Trust segmentation and third-party identity governance not just an IT control, but a fiduciary obligation.
4) Incident Economics Improved with Automation
Zero Trust approaches that coupled continuous verification with SOAR workflows (auto-revoking sessions, rotating secrets, quarantining assets) shaved minutes to hours off MTTR. At scale, those minutes translate into millions in avoided downtime relative to IBM’s cost baselines.
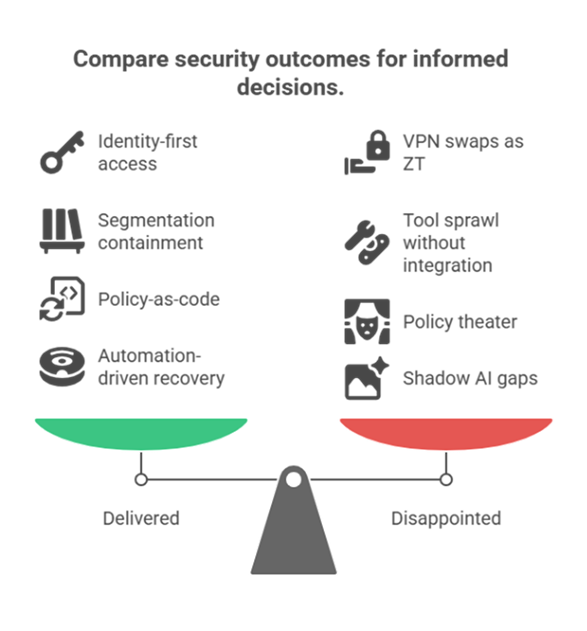
1) “Swap the VPN” ≠ Zero Trust
Many programs equated ZT with a perimeter-replacement tool. The result: network tunnels by another name, still granting broad reach once connected. Engineers then bypassed controls to stay productive, undercutting ZT’s least-privilege promise. (Remember the survey: 83% admitted workarounds; 90% cited VPN limits.) IT Pro
Fix: Make identity the new perimeter. Use short-lived tokens, step up authentication for sensitive actions, and explicitly disallow broad network inheritance from remote access.
2) Tool Sprawl Without Architecture
Organizations bought ZTNA, EDR, CSPM, and IAM add-ons – but never unified identity, logging, or data classification. When breaches cross SaaS, cloud, and on-premises environments, visibility gaps slow responders – exactly the scenario that drives multi-environment breach costs.
Fix: Fund the plumbing: normalize telemetry, reconcile identities, and label data before adding the next tool.
3) Policy Without People
ZT controls sometimes degrade the developer or operator experience. Predictably, users found routes around them (local secrets, ad-hoc tunnels). Sustainable ZT requires product-quality UX, including fast authentication, low-latency access, self-service enrollment, and streamlined workflows. The 2025 survey shows organizations trying to consolidate for efficiency – good news if it removes friction rather than adding it. IT Pro
4) AI and Shadow IT Outpaced Guardrails
In 2025, AI-related breaches (shadow AI, plugin/API chains) raised the bar for ZT: per-request authorization must cover data regression to models and agents, not just human users. Few teams had mature AI access controls, and breach costs rose accordingly. IT Pro
Fix: Treat AI systems as first-class principals in ZT: inventory models, govern prompts and outputs, and enforce least privilege on model-to-data access.
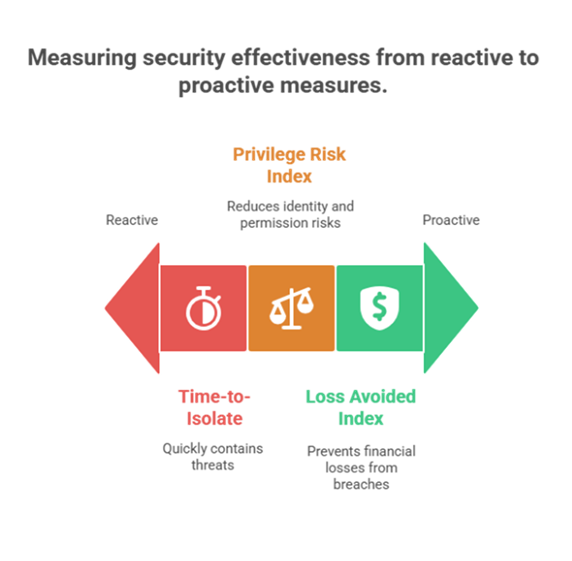
Boards in 2025 demanded outcome metrics, not slogans. A ZT program that “delivered” could show movement on a one-page scorecard:
These metrics tie directly to loss avoidance and resilience proof, translating Zero Trust into the finance-first language boards expect.
Federal guidance moved from principle to practice. The CISA ZTMM v2 provides agencies (and any large enterprise) with a staged path from traditional to advanced to optimal maturity. The DoD followed with renewed guidance in July 2025 to keep ZT on a resourced track toward 2027 targets. Even if you’re in the private sector, these artifacts are useful: they translate ZT into operational milestones that boards can audit.
Zero Trust remains the most credible blueprint we have for a world of hybrid work, AI-infused apps, and porous supply chains. But it pays off only when it’s implemented as architecture, measured as outcomes, and sustained as an operating model. NIST, CISA, and sector roadmaps give the scaffolding; your integration work supplies the value.
Turning Principles Into Proof
Enterprises need security partners who can align technical controls with board-level outcomes – identity clarity, segmentation efficacy, and time-to-isolate that can be proven. By combining AI-aware, identity-based access, micro segmentation, and compliance-ready reporting, partners like Compunnel help leaders turn Zero Trust from theory into evidence-backed resilience – with metrics the board understands.
In 2025, Zero Trust did not fail; many implementations did. The gap wasn’t a lack of vision – it was a matter of execution and evidence. Organizations that treated ZT as an operating system for security saw fewer privileges, smaller blast radii, faster recovery, and clearer audit trails. Those that didn’t see workarounds, visibility gaps, and multi-environment breaches that still cost millions.
As you plan 2026, measure your ZT program the way your board will:
If you can answer those questions with numbers and evidence, Zero Trust will continue to deliver. If not, it’s time to rebuild around identity, segmentation, automation – and a scorecard that proves it.
As boards demand results, explore how Compunnel Cybersecurity Services helps translate Zero Trust investments into measurable reductions in risk and time-to-recover – so you can show not just what you deployed, but what it changed.
