The 2025 Cyber ROI Reality Check: Why More Spend Didn’t Mean More Security
Introduction: Record Spend, Record Stress 2025 will be remembered as the year the cybersecurity budget line swelled, yet so did…
2025 reset the board conversation on cybersecurity. It was the year cyber reports had to graduate from rear-view mirrors to profit-and-loss statements. Directors don’t want logs; they want ledgers. “Blocked attacks” and “alerts handled” no longer satisfy leaders sitting under intensifying regulatory scrutiny and volatile operating conditions.
Boards now demand proof that security spend changes enterprise outcomes: lower loss expectancy, faster recovery, stronger compliance posture, and durable operations when, not if, an incident lands. Audit committees have elevated cybersecurity into their top-tier priorities and expect decision-grade metrics, not technical telemetry.
Two forces drove this shift. First, the cost and complexity of incidents remained stubbornly material; global breach costs averaged $4.45M (and $10.22 in the U.S.), with multi-environment attacks costing even more. Second, disclosure obligations tightened; the U.S. SEC expects Form 8-K reporting within four business days once an incident is deemed material, making cyber a capital-markets issue as much as a technical one.
What follows is a boardroom playbook: how to frame ROI, risk, and resilience with evidence, which proof points resonate, and what’s next as the language of proof evolves in 2026.
The ROI narrative that works
Stat to anchor the board discussion: Global average breach cost $4.44M; U.S. average $10.22 (2025). Multi-environment incidents remain the most expensive pattern.
In 2025, cyber risk was elevated from IT risk to enterprise risk. Directors want a defensible mapping from obligations and threats to specific controls and assurance evidence.
Regulatory proof
Third-party and supply-chain proof
Boards increasingly ask, “Where are we exposed through partners?” Use a tiered supplier model and present SBOM intake rates, attestation coverage, and access segmentation. Recent reporting indicates that roughly 30% of reported attacks in a major 2024 sample originated from third parties, with a growing trend continuing into 2025, a data point that directors can readily grasp.
Insider and AI-driven exposure
Bottom line: The risk conversation has moved from “Do we have a policy?” to “Show me the control and the evidence it works.”
Resilience is the ability to absorb, recover from, and adapt to stress. In 2025, it became the board’s preferred outcome.
What boards want to see
Why it matters financially
Ransomware payments may have decreased by 35% in 2024 to approximately $813.6 million; however, operational disruption and recovery costs continue to significantly impact quarterly performance. Resilience proves you can keep revenue-generating processes alive even as you remediate.
Directors aren’t asking for raw logs; they want concise, repeatable proof linked to enterprise value. Build a one-page scorecard and a reporting appendix.
Outcome metrics that resonate
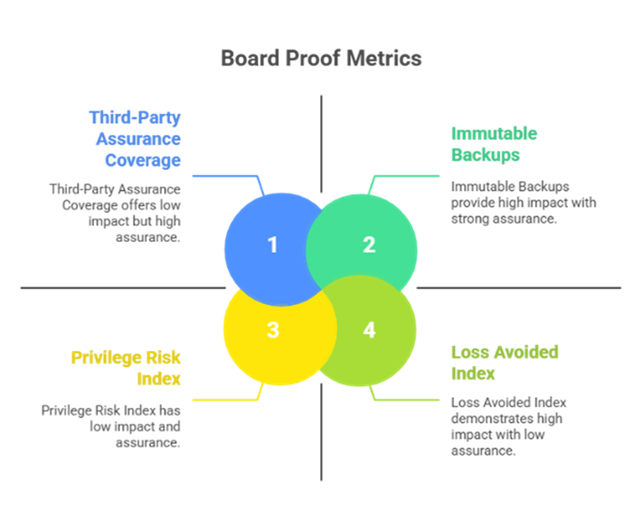
Tip: Put money next to every metric, loss avoided, downtime avoided, advisory fees avoided, or fines avoided. That’s the language of enterprise value.
When CISOs report outcomes instead of activities, three things happen:
AI governance becomes measurable. Boards will expect AI risk scorecards: model inventories, data lineages, red-team findings, precision/recall thresholds for security AI, and incident-response automation deltas (minutes saved per containment). The EU has made clear it will stick to the AI Act timeline; expect similar momentum in board agendas. Reuters
ESG-linked security disclosures mature. Cyber will increasingly appear in ESG and sustainability narratives, especially where operational resilience affects environmental or social outcomes (e.g., critical infrastructure outages). WEF guidance on resilience and system interdependencies foreshadows this integration.
Benchmarking normalizes. Directors will compare your cyber ROI and resilience metrics to peer ranges, including breach-cost deltas versus sector averages, time-to-file after materiality determination, and supplier-assurance coverage relative to industry practices. NACD and Big Four board briefings are already pushing toward standardized board-level cyber metrics.
Supply-chain proofs get deeper. Following a wave of third-party incidents, boards will require artifact-level assurances, including SBOMs, attestation evidence, and compensating controls for high-risk vendors. Regulators’ NIS2 enforcement and sector guidance will further formalize expectations.
Incident economics trump payment trends. Even as ransomware payouts dipped to approximately $813.6 million in 2024, boards will continue to spotlight downtime and recovery, as that’s what drives earnings volatility. Your 2026 plans should prove shorter recovery arcs and ring-fenced critical services.
Boards will also normalize talent resilience metrics, from offer-acceptance rates for critical roles to analyst hours saved via automation, as workforce gaps remain a systemic limiter.
Enterprises need security partners who can align technical controls with ROI and risk frameworks, areas where Compunnel has built measurable, board-ready solutions. By combining AI-driven monitoring with compliance-ready reporting (SEC mock 8-Ks, GDPR/AI-Act evidence pipelines) and supplier-assurance artifacts, Compunnel helps leadership teams speak the board’s language of ROI, risk, and resilience, and prove it quarter after quarter.
2025 taught directors and executives the same lesson: proof beats promise. Boards now expect cybersecurity to demonstrate return on resilience, lower loss expectancy, faster recoveries, cleaner compliance, and safer ecosystems. The metrics are available; the discipline is achievable. What differentiates leaders is their ability to connect investments to outcomes with evidence, rather than relying on anecdotes.
And with frameworks like NIS2 making directors themselves liable for third-party oversight, proof isn’t just operational, it’s fiduciary. Boards want evidence in dollars saved, downtime avoided, and fines reduced, not just tool counts or policy binders.
As boards demand more proof, CISOs need partners who can help translate cybersecurity investments into enterprise value. Explore how Compunnel Cybersecurity Services can support this transformation, so your next board deck doesn’t just report activity; it proves performance.
