Supply Chain Breaches 2025: The Weakest Links That Cost Millions
Introduction: When “One Vendor Away” Became Everyone’s Risk If 2024 was the year third-party risk went mainstream, 2025 made it…
2025 will be remembered as the year the cybersecurity budget line swelled, yet so did the headlines. Global security and risk management spend climbed to roughly $213 billion, driven by board anxiety, AI-fueled threats, and expanding compliance mandates. However, despite larger checks, organizations continued to struggle with ransomware, sprawling multi-cloud risks, and regulatory missteps.
CISOs discovered in 2025 that cybersecurity budgeting was less a safety net and more a treadmill: spend more, run harder, and still fall behind. The uncomfortable truth surfaced across boardrooms: more spending didn’t automatically translate into better outcomes.
Meanwhile, the breach ledger remained stubborn. IBM’s 2025 research pegged the global average cost of a data breach at approximately $4.4 million, down year over year, but still substantial, and highlighted how breaches spanning multiple environments averaged $5.05 million and lasted longer. In the U.S., the average breach cost reached a record $ 10.22 million. In parallel, ransomware payments decreased by 35% in 2024 to approximately $813.6 million, but extortion continued to cause material disruption and incur significant recovery costs.
Boards and CFOs, understandably, began asking more complex questions: If we’re spending more, where’s the risk reduction? Which controls actually changed outcomes? What are we getting for each incremental dollar?
A left-to-right view of how record cybersecurity spend flowed into tool sprawl, compliance hours, and integration gaps, with limited risk reduction to show for it.
Overinvestment in Tools, Underspending on Architecture
Organizations layered products across identity, EDR, email, and cloud posture, but left identity sprawl and data mapping unresolved. When incidents occur, responders chase symptoms across consoles while attackers pivot through unmanaged service principals or stale SaaS sessions. The cost signal breaches, spanning on-premises, cloud, and SaaS, averaged $5.05M, the highest of any pattern.
ROI fix: Fund integration and rationalization programs-unify identity, logging, and data classification before adding the next sensor. Measure success with hard outcomes: fewer admin-equivalent identities, reductions in unused high-risk entitlements, and shorter investigation times.
KPIs Without a CFO Lens
Security teams reported activity throughput while boards wanted loss-avoidance math: “How did this investment reduce downtime or legal exposure?” Guidance in 2025 pushed leaders to express cyber risk in business terms, mapping key metrics to dollars and strategy (e.g., probability-weighted loss per service).
ROI fix: Recast metrics into three tiers: resilience (RTO/RPO performance), exposure (toxic combinations of permissions, crown-jewel control failures), and efficiency (automation coverage and analyst hours saved). Tie each to projected and realized loss reduction.
Compliance as Output, Not Outcome
SEC disclosures and GDPR enforcement forced rigor in incident handling and transparency. Yet, they sometimes spend time clustered around reporting artifacts rather than preventive controls, leaving attack paths intact. GDPR penalties continued to mount, reaching a cumulative total of €6.7B by October 2025, highlighting the increasing cost of gaps that paperwork couldn’t plug.
ROI fix: Treat compliance as assurance of control efficacy. For each obligation, trace to a technical safeguard and evidence pipeline (e.g., least-privilege attestations, immutable backup tests). Report the control, not just the compliance.
AI Hype vs. AI Health
In 2025, many teams piloted AI copilots for Tier-1 triage and enrichment, but without model governance, data guardrails, or measurement of analyst lift. The result: new tools, limited uplift, and added oversight burden. Industry surveys warned that defenses were not keeping pace with AI-enabled threats; some organizations introduced AI without clear success criteria. T
ROI fix: Define AI OKRs up front: percentage of alerts auto-triaged to closure, minutes saved per investigation, false-positive reduction, and changes in MTTR. Build privacy and safety checks into prompts, data stores, and outputs.
Workforce Pressure
With only ~74% of open roles filled at many large enterprises and a global shortfall of more than 3.5 million cybersecurity positions, teams fell behind on hygiene, threat hunting, and tabletop exercises, which are classic lagging indicators before incidents. Studies have associated staffing shortages with an average of $1.7 M higher breach costs.
ROI fix: Shift from headcount-only thinking to automation + role redesign. Fund playbook automation (containment, session revocation, sandboxing) and measure reclaimed analyst hours and backlog burn-down.
KPIs Without a CFO Lens
Security teams reported activity throughput while boards wanted loss-avoidance math: “How did this investment reduce downtime or legal exposure?” Guidance in 2025 pushed leaders to express cyber risk in business terms, mapping key metrics to dollars and strategy (e.g., probability-weighted loss per service).
ROI fix: Recast metrics into three tiers: resilience (RTO/RPO performance), exposure (toxic combinations of permissions, crown-jewel control failures), and efficiency (automation coverage and analyst hours saved). Tie each to projected and realized loss reduction.
Compliance as Output, Not Outcome
SEC disclosures and GDPR enforcement forced rigor in incident handling and transparency. Yet, they sometimes spend time clustered around reporting artifacts rather than preventive controls, leaving attack paths intact. GDPR penalties continued to mount, reaching a cumulative total of €6.7B by October 2025, highlighting the increasing cost of gaps that paperwork couldn’t plug.
ROI fix: Treat compliance as assurance of control efficacy. For each obligation, trace to a technical safeguard and evidence pipeline (e.g., least-privilege attestations, immutable backup tests). Report the control, not just the compliance.
AI Hype vs. AI Health
In 2025, many teams piloted AI copilots for Tier-1 triage and enrichment, but without model governance, data guardrails, or measurement of analyst lift. The result: new tools, limited uplift, and added oversight burden. Industry surveys warned that defenses were not keeping pace with AI-enabled threats; some organizations introduced AI without clear success criteria. T
ROI fix: Define AI OKRs up front: percentage of alerts auto-triaged to closure, minutes saved per investigation, false-positive reduction, and changes in MTTR. Build privacy and safety checks into prompts, data stores, and outputs.
Workforce Pressure
With only ~74% of open roles filled at many large enterprises and a global shortfall of more than 3.5 million cybersecurity positions, teams fell behind on hygiene, threat hunting, and tabletop exercises, which are classic lagging indicators before incidents. Studies have associated staffing shortages with an average of $1.7 M higher breach costs.
ROI fix: Shift from headcount-only thinking to automation + role redesign. Fund playbook automation (containment, session revocation, sandboxing) and measure reclaimed analyst hours and backlog burn-down.
Stats callouts (2025):
• $213B – Estimated global security & risk spend in 2025.
• $4.5M – Global average cost of a data breach. $5.05M when multi-environment. U.S. average $10.22M.
• −35% – Drop in ransomware payments in 2024 vs. 2023 (to $813.6), even as operational disruption remains high.
• €6.7B – Cumulative GDPR fines by Oct 2025.
Case-Style Insight #1: The Multi-Cloud Mirage
A global manufacturer spent eight figures building a next-gen SOC and buying best-in-class tools. But it never normalized identity and logging across two clouds and a legacy directory. When ransomware infiltrated via a compromised contractor account, responders were unable to detect lateral movement between SaaS sessions and cloud workloads. Two plants stalled; the incident cost exceeded seven figures. The board’s lesson: platform integration first, tools second. (Pattern consistent with higher costs for multi-environment breaches.)
Case-Style Insight #2: Compliance without Control
A public company prioritized SEC readiness: playbooks, counsel, and disclosure templates. But a privileged-access review for a crown-jewel ERP instance kept slipping. When a supplier’s email account was compromised, attackers reused a dormant admin token. The company filed promptly, but it still incurred reputational damage and remediation costs. The lesson: disclosure is not a defense. (Context: SEC four-business-day disclosure requirements increased governance pressure.)
Case-Style Insight #3: AI Adoption, Minimal Lift
A financial services firm rolled out AI triage to cut Tier-1 workload. Without outcome metrics, it couldn’t demonstrate value. Analysts didn’t trust the recommendations, so they manually reworked cases. Only after defining precision/recall targets, capturing the minutes saved per alert, and tuning on curated data did MTTR drop meaningfully. (Broader 2025 narrative: robust adoption, uneven maturity.)
1) Rebalance the Portfolio Around Outcomes
From tools to outcomes: Tie budget requests to explicit loss-avoidance models (e.g., “Identity hardening reduces probability of lateral movement by X%, translating to $Y in expected loss reduction per year.”). Require post-implementation reviews that show MTTR reductions and incident cost deltas.
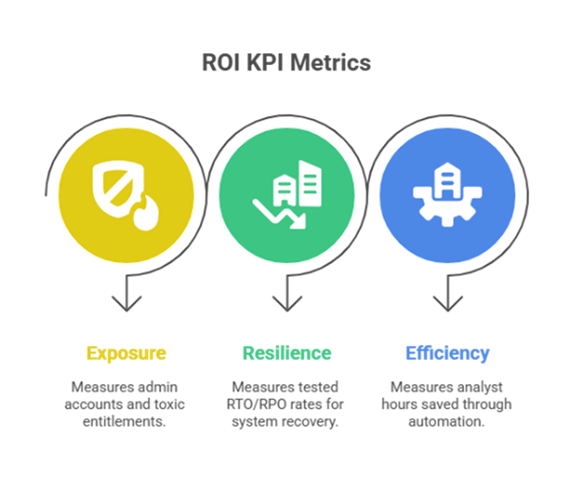
Boards no longer accept activity counts. They want outcome KPIs: Exposure reduced, Resilience tested, and Efficiency gained.
KPIs to adopt:
(These align to board-level guidance on metrics that matter.)
2) Integrate Identity, Telemetry, and Data
Stand up a unified identity fabric for human and non-human actors (service principals, bots). Normalize logs into a common data model across cloud, SaaS, and endpoint to accelerate correlation. Map and label sensitive data to prioritize materiality in investigations.
Expected ROI: Faster containment, fewer false positives, and lower average breach cost in multi-environment incidents, the most expensive class.
3) Automate the Repetitive 80%
Instrument SOAR or workflow automation for credential revocation, SaaS session kills, quarantine, and isolation. Track reclaimed analyst time monthly and apply it to threat hunting and control validation. Outcome target: reduce MTTR by 25–40% for top-quartile incident types.
4) Align Compliance with Control Evidence
Build evidence pipelines that satisfy SEC and GDPR requirements, demonstrating control performance through immutable backup test logs, least-privilege attestations, third-party access reviews, and tabletop exercises. Measure reduction in audit findings and time-to-file for disclosures to cut advisory costs and reputational risk. T
5) Make AI Accountable
Adopt AI OKRs that specify precision/recall thresholds, minutes saved per Tier-1 alert, and target MTTR improvements. Establish data handling rules for prompts, logs, and outputs to ensure consistency and accuracy. Utilize small, high-value pilots in phishing triage and EDR enrichment to demonstrate lift, then scale them up. (2025 showed adoption is widespread; 2026 must show measured benefit.)
6) Close the Human Gap with Design and Flexibility
Refresh hiring practices (including remote options, modern job titles, and compensation transparency), and automate repetitive tasks to curb burnout. Treat workforce metrics-on-call load, training hours, automation coverage- as leading indicators of incident performance. (Large-enterprise data shows only ~74% of roles are filled; modernizing practices expand the funnel.)
The budget conversation has changed. With spending at an all-time high and breach costs stubborn, boards and CFOs now demand evidence-backed ROI:
This discipline is not punitive-it’s how cyber becomes a business enabler in 2026 and beyond.
Enterprises need solutions that not only defend but also demonstrate value, a concept that Compunnel emphasizes through outcome-driven cybersecurity services. By aligning investments to measurable metrics (exposure, resilience, efficiency) and implementing AI-native monitoring with compliance-ready evidence pipelines, partners like Compunnel help leaders prove ROI while strengthening resilience. The focus is on integration over tool sprawl, governance over hype, and automation that gives scarce talent back the time it matters most. (Context: widespread AI adoption, SEC/GDPR pressures, and multi-environment breach costs.)
2025 exposed a simple truth: spend is a means, not an outcome. Big budgets didn’t stop ransomware from disrupting operations, nor did they prevent multi-environment breaches from costing millions of dollars. Organizations that did bend their risk curves focused relentlessly on outcomes, integrating identity and telemetry, automating containment, leveraging AI with clear OKRs, and ensuring compliance was anchored in control evidence, not paperwork.
Boards now want proof in dollars saved, downtime avoided, and breach costs reduced, not just lists of licenses purchased.
As you plan 2026, redirect the conversation from “How much should we spend?” to “What will this investment change, and how will we prove it?” Set outcome targets, measure relentlessly, and retire low-yield controls.
If you want a partner to help turn cybersecurity spending into measurable resilience, compliance, and business protection, explore how Compunnel aligns security investments with results, so you can show your board not just what you bought, but what you achieved.
