Looking Back to 2025: The Threat Landscape That Tested Every CISO
Introduction: Why 2025 Stood Out If 2024 felt relentless, 2025 proved it could be worse- and, paradoxically, more complicated. CISOs…
If 2024 was the year third-party risk went mainstream, 2025 made it a visceral reality. Directors watched as marquee manufacturers halted production, software ecosystems reeled from package-registry compromises, and disclosure rules highlighted how a single partner could ripple into material revenue loss. In surveys and post-mortems, the through line was clear: supply chains, both physical and digital, were the soft underbelly of enterprise resilience. More than seven in ten organizations reported at least one material third-party cyber incident in the prior year; fewer than half had visibility into even half of their third-party dependencies.
This piece distills what went wrong in 2025, the patterns that amplified loss, and how leaders can strengthen the connections that actually drive the business.
Manufacturing stoppages with economy-scale consequences
Late summer and September saw one of the starkest illustrations: a UK automotive giant paused production across plants, costing tens of millions of pounds per day and threatening jobs across a supplier base exceeding 100,000. Press estimates tallied ~24,000 undelivered cars and ~£1.7–£2.2 billion in revenue impacts by early fall, numbers that put “cyber risk” squarely on earnings calls. The incident wasn’t isolated in its effect: stoppages strained the cash flow of small suppliers, forcing them to seek emergency financing and consult with the government.
Software supply chain shock: npm “worm” in the wild
On the digital side, the world’s largest JavaScript registry faced a self-replicating worm (“Shai-Hulud”) that compromised hundreds of packages and over 500, according to a U.S. government count—highlighting how developer ecosystems can propagate risk at machine speed into CI/CD pipelines and production. CISA+1
Macro signal: third-party breaches are rising
Independent analyses quantified the momentum: 35.5% of breaches in 2024 involved third-party access (up 6.5% YoY), and 41.4% of ransomware attacks leveraged a partner foothold—trends that continued to shape 2025 risk registers.
Stats callouts (2025):
1) Point-in-time assurance in a real-time world
Most programs still rely on annual questionnaires and vendor self-attestations. The SecurityScorecard 2025 study found that only 26% of organizations embed incident response into third-party risk management (TPRM), and fewer than half monitor even 50% of their third-party dependencies. That leaves blind spots exactly where attackers look.
2) “Everything has an API”, and too many keys
Partners, integrators, and managed service providers routinely hold persistent, high-privilege tokens in production services. Identity sprawl—encompassing service principals, personal access tokens, and forgotten OAuth grants—means that a single compromised contractor account can potentially bridge SaaS, cloud, and OT networks.
3) Build systems as blast radiators
Modern delivery pipelines pull code from public registries, run ephemeral builds using shared runners, and then deploy to multiple clouds. Without provenance checks (SLSA, provenance attestations), one poisoned package can infect dozens of microservices and hundreds of tenants downstream.
4) Resilience untested with suppliers
Backups and failover are often proven internally, not end-to-end, with critical vendors. When a supplier outage cascades, many enterprises discover the hard way that their RTOs assume cooperation, but the contract doesn’t enforce it.
5) Compliance ≠ control
Regimes like NIS2 push supplier due diligence and reporting, but implementation is uneven across member states. Many organizations spent 2025 mapping scope and drafting policies rather than instrumenting evidence (e.g., SBOM intake rates, attestation freshness), resulting in compliance activities without risk reduction.
The global average cost of a data breach in 2025 was approximately $4.45 million, but breaches spanning multiple environments (on-premises, cloud, and SaaS) averaged around $5.05 million and took longer to contain. Chain intrusions often fall into this costly category. U.S. organizations faced an average of $10.22.
Manufacturing stoppages convert instantly into lost output and unabsorbed fixed costs, as the automotive case underscored. For digital supply shocks (e.g., package registry events), risk is nonlinear: a single dependency break can simultaneously stall dozens of internal teams.
GDPR enforcement has continued to accumulate in the billions of euros since 2018, reminding boards that third-party handling of personal data doesn’t transfer liability. A 2025 legal survey reported cumulative GDPR fines of nearly €5.9B as of early 2025, with totals continuing to rise throughout the year. DLA Piper
With the U.S. SEC mandating four-business-day disclosures after a materiality determination, third-party incidents can become market events. Legal, advisory, and investor relations costs accumulate even when the initial compromise is located “outside your four walls.”
2. Opaque software components
3. Unmonitored third-party exposure
4. No kill switch for partner incidents
5. Recovery proven without the ecosystem
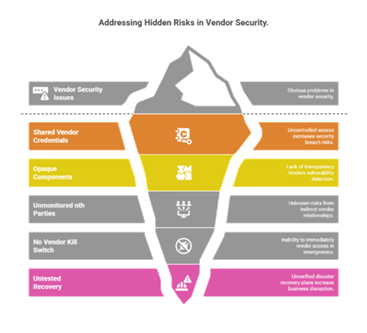
A manufacturer with world-class internal controls inherited a supplier breach through an engineering services firm. A reused admin token enabled lateral movement into a production scheduling system. Two plants paused for nearly a week, incurring contractual penalties for both parties. What failed: vendor token hygiene and lack of egress control on partner sessions. What would have helped: short-lived credentials, conditional access, and a vendor kill switch.
A SaaS company’s CI pulled a popular npm library tainted by the Shai-Hulud worm. Malicious pre-install scripts exfiltrated secrets, forcing a rotation storm and delaying a flagship release by a sprint. What failed: provenance checks and secret scanning. What worked after: SBOM enforcement at pull request, Sigstore/Cosign signing, least-privileged build runners, and mandatory secret zero rotation for anomalous package behavior.
A healthcare firm passed vendor questionnaires but never validated the freshness of the evidence. A records digitization partner suffered a ransomware attack, exposing protected health information. The firm filed disclosures, faced regulatory scrutiny, and absorbed breach costs that were well above the average. What failed: reliance on point – in – time attestations; no IR integration in TPRM. What would have helped: continuous assurance (attack surface monitoring), periodic tabletops with vendors, and immutable backup verification tied to RTOs.
1) Make visibility continuous, and include nth parties
Move beyond annual surveys. Combine external risk telemetry (exposed services, expired certs, leaked creds) with targeted evidence requests. Track a Third-Party Assurance Coverage metric: % of Tier – 1/1/Tier/2 suppliers with up-to-date SBOMs, recent penetration testing artifacts, and incident-response contacts on file.
2) Turn contracts into controls
Bake right-to-disconnect, time-boxed access, SBOM delivery, and notification SLAs into MSAs and renewals. For critical vendors, require coordinated IR table-tops and quarterly restore drills. Align to NIS2 where relevant to keep pace with EU expectations around supplier oversight.
3) Engineer a vendor kill switch
Pre-stage automation that, on a supplier incident flag, will:
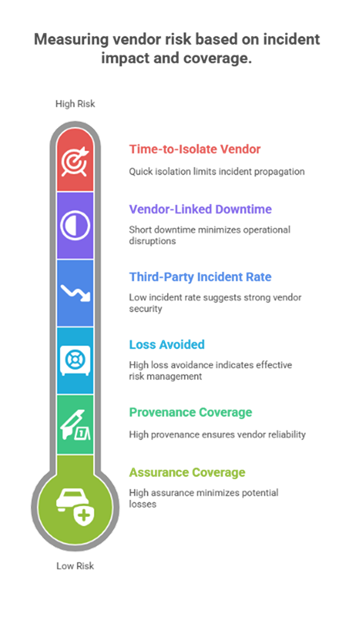
Measure time-to-isolate and blast radius (identities and assets affected) as board-level KPIs.
4) Secure the software factory
Adopt SLSA – aligned provenance, sign builds (e.g., cosign), and enforce policy at merge and deployment. Block unsigned or unknown – provenance packages. Track “% of deployed artifacts with verified provenance” as a reliability and security metric, especially after the npm incident.
5) Tie resilience to money
Express RTO attainment and end – to – end recovery time (with suppliers) in revenue minutes saved. Boards respond to dollars: show how reducing a critical vendor’s recovery window from 16 to 6 hours avoids X in lost bookings in peak periods.
6) Align compliance with evidence pipelines
For GDPR/NIS2/SEC contexts, automate the capture of control evidence (immutable backup checks, least-privilege attestations, supplier access reviews). This reduces advisory hours and accelerates the time-to-file without stealing cycles from factual defenses.
Keep the dashboard one page for directors, with an appendix for practitioners.
Enterprises need security partners who align technical controls with third-party governance and can demonstrate this alignment with evidence. Providers like Compunnel emphasize outcome-driven supply-chain security: AI-assisted monitoring of external risk signals, SBOM, and provenance enforcement in software delivery, identity-first vendor access, and compliance-ready reporting (NIS2/GDPR/SEC). The focus is practical: shorten time-to-isolate, raise assurance coverage, and demonstrate loss-avoided metrics that resonate in the boardroom.
2025’s lesson is blunt: Your enterprise’s resilience is only as strong as the partners who can reach your data, run your code, or pause your production. Physical suppliers can stall factories; package registries can taint pipelines; managed service providers can bridge networks. The costs are measured in millions, ranging from breach forensics to lost output, fines, and disclosure overhead.
The path forward is equally clear:
Boards now expect proof in the form of dollars saved, downtime avoided, and recovery accelerated, not just lists of tools deployed. CISOs who can show loss avoided as a measurable KPI will secure both budget and board confidence.
Suppose you’re ready to translate supply-chain spending into measurable resilience. In that case, Compunnel Cybersecurity Services can help align TPRM, identity, provenance, and recovery into a single outcome: an enterprise that remains resilient when the weakest link is compromised.
