Supply Chain Breaches 2025: The Weakest Links That Cost Millions
If 2024 was the year third-party risk went mainstream, 2025 made it a visceral reality. Directors watched as marquee manufacturers…
If 2024 felt relentless, 2025 proved it could be worse- and, paradoxically, more complicated. CISOs walked a tightrope between a generative AI gold rush, tightening regulations, and a macro environment where supply chain shocks and ransomware disruptions could impact revenue in a single quarter. The year’s data paints a stark picture: the global average cost of a data breach hovered around $4.45M, with multi-environment incidents costing even more and lasting longer. Meanwhile, the EU doubled down on the AI Act’s phased obligations, and the SEC’s four-day disclosure rule kept boards- and IR playbooks- on edge.
This retrospective distills the top 6 threats that defined 2025 and what they mean for enterprise risk, ROI, and resilience in 2026.
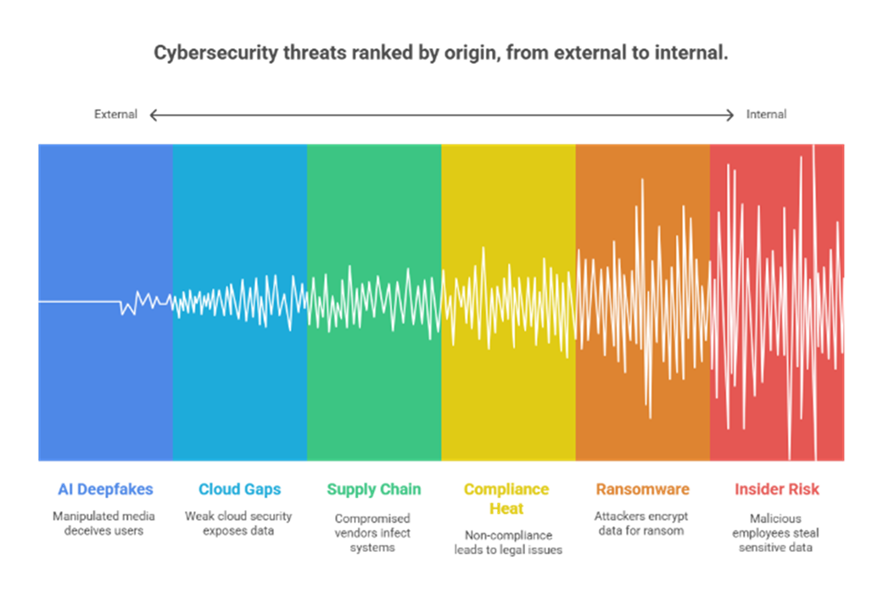
1) AI-Powered Attacks & Deepfake-Driven Phishing
Generative AI didn’t just help defenders; it supercharged adversaries. Deepfake voice and video have matured from novelty to an operational tool, lowering the barrier for Business Email Compromise (BEC) and executive impersonation fraud. Several data points underline the shift:
Why it matters: AI collapses the cost of persuasion. Attackers now produce fluent, on-brand, and timely lures at scale, often combining voice cloning, synthetic video, and real company context scraped from public sources.
Controls that moved the needle in 2025:
2) Cloud Security Gaps in Hybrid/Multi-Cloud
Multi-cloud is the default- but consistent control is not. In 2025, 55% of organizations reported using two or more cloud providers, while misconfiguration and identity weaknesses remained top risk drivers. Surveys and compilations indicate that ~23% of cloud incidents originated from misconfigurations; many teams continue to struggle with maintaining uniform controls across providers.
Why it matters: Misaligned IAM, overlooked API keys, and inconsistent logging create “gray zones” attackers love- especially when workloads span multiple platforms.
What worked in 2025:
3) Insider Threats Amplified by Remote & Hybrid Work
The insider risk story sharpened this year. Ponemon’s 2025 analysis pegged the average annual cost of insider incidents at $17.4M per organization, while containment times finally ticked down (to ~81 days) but remained too slow for high-value data. Malicious insider incidents and credential theft continued to drive the most expensive outcomes, particularly when access governance was inadequate.
Complementary research in 2025 also reported material bottom-line impacts from insider events, with average incident losses in the $2.7M range for many firms- a reminder that file-based data leakage is both common and costly.
Why it matters: Remote collaboration tools, generative AI copilots, and sprawling data lakes have increased the attack surface for both negligent insiders and those abusing trust.
Controls that worked:
4) Ransomware-as-a-Service (RaaS) Evolved- Even as Payouts Shifted
The economics of ransomware changed shape. Law-enforcement disruption and “don’t pay” policies pressured payouts downward year-over-year, yet operator counts and victim disclosures remained high:
Why it matters: Even when payments drop, business interruption and forensic/IR/RTO costs remain huge. Attackers are increasingly combining data theft, DDoS attacks, and harassment to force negotiations.
Defenses that improved outcomes:
5) Compliance Heat: AI Act, NIS2 & SEC Disclosures
2025 was the year compliance became an operational attack surface. The EU AI Act advanced on a fixed timeline, with prohibitions and AI literacy rules taking effect from February 2, 2025; GPAI obligations from August 2, 2025; full applicability from August 2, 2026; and high-risk AI from August 2, 2027. The Commission reiterated that there would be no delays despite industry requests.
In parallel, the SEC’s cybersecurity rule continued to shape disclosure practices: material incidents require Form 8-K, Item 1.05, to be filed within four business days of the materiality determination, influencing IR runbooks and board oversight. Analysis in 2025 highlighted how companies increasingly route non-material events to Item 8.01 and how the enforcement landscape is evolving.
Across the EU, NIS2 obligations expanded, with uneven national transposition, but rising expectations for risk management and reporting- plus 2025 registration milestones for in-scope entities.
Why it matters: Regulatory non-compliance now compounds cyber loss- through fines, disclosure-driven reputational damage, and litigation risk. CISOs had to harmonize technical controls, AI governance, and legal process.
6) Supply Chain & Third-Party Vulnerabilities
Adversaries kept going “through the partner to hit the prize.” Headlines late in the year reinforced the stakes: a major automaker paused production across plants, with multi-billion-pound revenue impacts and cascading stress on suppliers; npm ecosystems saw self-replicating malware riding trusted packages; and reporting highlighted that ~30% of reported attacks in 2024 originated via third parties- a share that rose sharply year-over-year.
Longer-horizon research echoed the same arc: software supply-chain attacks are accelerating, with Gartner predicting widespread exposure by 2025 and multiple industry reports warning of steep increases in cost and frequency.
What reduced exposure:
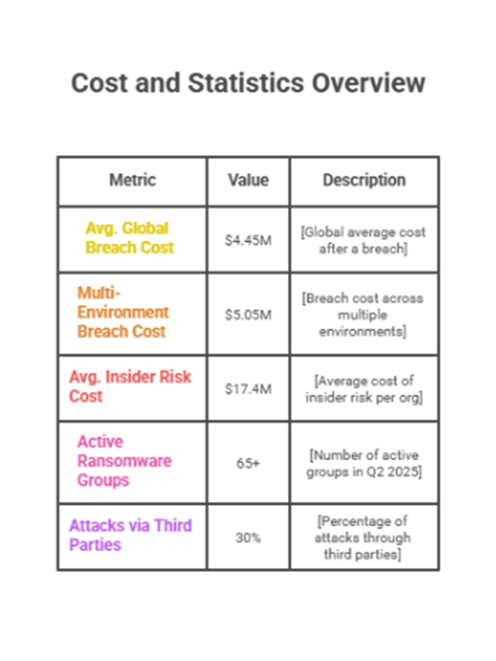
Cost per breach: The global average cost was approximately $4.45 million. Incidents that spanned multiple environments (on-prem + cloud + SaaS) averaged ~$5.05M and took longer to contain- evidence that architectural complexity taxes IR.
Operational disruption: Manufacturing and critical services experienced significant downtime and revenue loss, as indicated by sector threat indices and real-world stoppages; ransomware continued to be a top driver of extortion and production pauses.
Reputational damage & compliance risk: Accelerated regulatory disclosures brought immediate market scrutiny; firms that mishandled materiality determinations or transparency took additional hits from investors and plaintiffs’ attorneys.
Productivity drain: Insider incidents and AI-assisted phishing forced re-authentication burns, emergency permission reviews, and workforce comms that sapped time from roadmaps- often for weeks. Multiple studies have quantified the multi-million-dollar impacts of insider data leakage alone.
Stats callouts (2025):
• $4.45M – Avg. cost of a data breach (global).
• $5.05M – Avg. cost when breaches spanned multiple environments.
• $17.4M – Avg. annual insider-risk cost per organization.
• >65 – Active ransomware groups in Q2; +41% 1H YoY.
• 30% – Share of reported attacks via third parties (2024 data, rising into 2025).
1) Treat AI as Both Asset and Liability
2) Collapse Multi-Cloud Risk with Identity & Data Controls
3) Institutionalize Insider Risk Management
4) Ransomware Resilience is a Board Metric
5) Make Compliance a Competitive Advantage
6) Harden the Supply Chain You Actually Have
As enterprises plan for 2026, leaders will need partners who can combine proactive monitoring, compliance readiness, AI-aware defenses, and third-party risk reduction- areas where providers like Compunnel are already delivering measurable impact. The emphasis is on identity-first security, cloud posture management, insider risk programs, and regulatory reporting readiness- all integrated to improve time-to-detect, time-to-contain, and auditability without over-rotating toward tool sprawl.
2025 tested every CISO’s mettle. AI supercharged social engineering, multi-cloud complexity exposed identity seams, insider risk matured, RaaS continued to innovate, compliance moved faster than many programs, and supply-chain weak links became front-page business risks. The data is unambiguous: complexity magnifies cost, and resilience pays for itself when measured against downtime, disclosure, and reputational drag.
In 2026, boards won’t measure CISOs by the number of tools they deploy – but by how quickly incidents are detected, contained, and disclosed. Time-to-detect, time-to-contain, and audit-readiness will be the KPIs that define credibility at the top table.
The playbook for 2026 is clear:
Suppose you’re ready to turn those KPIs into board-level proof. In that case, Compunnel’s Cybersecurity Services can help you standardize multi-cloud controls, operationalize insider-risk programs, harden supply chains, and build compliance into your architecture. So security becomes a multiplier for growth, not a drag on it.
