Contingent Workforce Solutions in 2026: How Enterprises Are Building Agile Talent Models
As we enter January 2026, the traditional corporate "headcount plan" is undergoing a quiet but radical retirement. For decades, the…
In 2025, the average employee manages more than 150 passwords, and still, 80% of cyber incidents trace back to compromised credentials. Enterprises invest millions in multi-factor authentication and password policies yet somehow end up increasing login prompts instead of reducing risk. What should have been stronger security often becomes a drag on productivity and a fresh set of vulnerabilities.
But the real issue has never been passwords. It’s the identities behind them – scattered across SaaS platforms, cloud apps, and legacy systems with no single source of oversight. This identity sprawl is now a bigger threat than brute-force attacks, quietly expanding the attack surface while traditional defenses remain unaddressed.
That’s where Identity and Access Management (IAM) shifts the conversation. Done right, IAM is not just about access control. It’s a trust framework, one that eliminates identity debt, restores visibility, and builds a security posture that scales with the modern workforce.
The Problem Was Never Passwords – It’s Identities.
While organizations invest heavily in perimeter defenses and enforce multi-factor authentication, one risk continues to grow silently: identity sprawl. A 2025 audit by the Enterprise Access Risk Council found that 62% of organizations failed to align user access with current job roles, with periodic access reviews either delayed or overlooked in one-third of cases.
It’s rarely the result of a single failure – instead, it builds through routine operational decisions:
Individually, these aren’t breaches. Collectively, they erode control and visibility over who can access what.
Over time, identities accumulate across cloud platforms, internal systems, and third-party applications. The result is:
Traditional security tools can’t catch this drift. Firewalls protect traffic, and endpoint tools monitor devices. However, Gartner predicts that 75% of security failures in 2025 will stem from inadequate identity management, rather than network or endpoint flaws. Identity sprawl grows silently, deep within the organization’s access fabric, steadily increasing its attack surface.
This is where Identity and Access Management (IAM) becomes relevant – not as a gatekeeper, but as a mechanism for restoring visibility. IAM brings structure to access chaos by mapping permissions to roles, enforcing time-bound policies, and automating offboarding workflows that are too often handled manually.
In practice, IAM makes identity sprawl visible and actionable by identifying attributes like:
The shift doesn’t require sweeping changes overnight. It requires a governance layer that prioritizes clarity before enforcement. IAM doesn’t solve sprawl by policing it; it solves it by finally making it measurable.
If identity sprawl is the mess we see, identity debt is what quietly accumulates beneath it, the backlog of unused credentials, stale permissions, and legacy access rights that never got cleaned up. These aren’t just leftovers – they’re overlooked liabilities.
In most teams, granting access is faster than revoking it. Removal often requires approvals, documentation, and bandwidth that are not readily available in real-time. So, access stays, and the backlog grows.
According to Gartner’s 2025 IAM forecast, 75% of security failures this year are linked to poor identity governance. And in an ISACA mid-2025 survey, 68% of enterprises admitted to carrying significant “identity debt” – unused accounts and outdated rights that accumulate faster than they can be reviewed.
The result isn’t just a security issue – it’s operational drag:
IAM doesn’t erase debt overnight. However, it prevents new debt from forming and gradually reduces the backlog through lifecycle-linked provisioning, auto-expiring temporary access, and real-time revocation triggers.
Fixing sprawl and debt is necessary, but by late 2025, IAM has evolved into something bigger: a frontline detection system and a compliance safeguard.
IAM is no longer just operational hygiene. It is a board-level compliance control and a real-time threat detection layer.
So far, we’ve looked at how identity sprawl expands and how identity debt accumulates. Beneath both lies a mindset problem: too many organizations still see identity as a binary gate – locked or unlocked.
However, in today’s hybrid, API-connected workplace, framing no longer holds. Modern teams need flexibility without blind spots. Collaboration without chaos. This is where traditional access control falls short.
IAM, when designed thoughtfully, doesn’t just restrict access – it builds structure around how trust is granted, used, and revoked.
What that looks like in practice:
The result: fewer assumptions, more accountability, and less friction. When trust is systematized, people don’t fight for access, and security teams don’t waste energy cleaning up after it.
And now, with ITDR and regulatory oversight in play, IAM isn’t just a control layer. It’s a trust framework, a compliance safeguard, and a detection system – aligning security with how modern work actually happens.
IAM Delivers More Than Access Control.
The password problem may have sparked the conversation, but identity is now the battlefield. Sprawl and debt remain costly, but the stakes have risen: regulators demand faster disclosures, investors expect airtight governance, and attackers target identities as their easiest entry point.
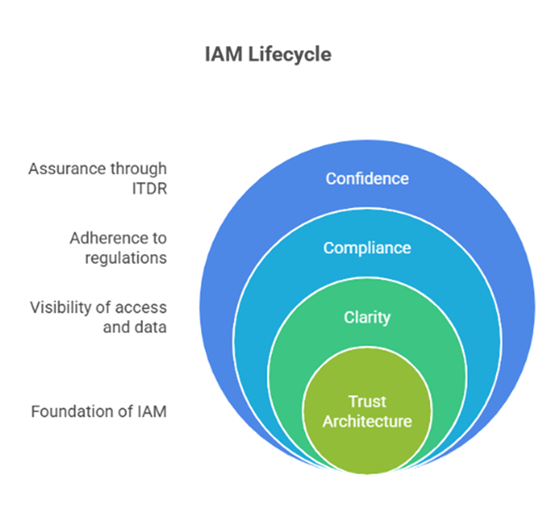
IAM’s evolution reflects this reality. It is no longer just an operational tool for IT teams – it is a strategic control for CFOs, CISOs, and boards alike. A mature IAM program now delivers three outcomes:
Enterprises that treat IAM as a living trust architecture, adaptive, predictive, and invisible, will move faster, stay compliant, and protect more with less friction. In 2026, security won’t be judged by how many accounts you control, but by how confidently your enterprise can prove who has access, why, and for how long.
That’s where Compunnel’s Cybersecurity Services come in. From identity governance to compliance intelligence, we help enterprises transition from reactive fixes to proactive resilience, turning IAM into a foundation for trust, security, and growth.
