Contingent Workforce Solutions in 2026: How Enterprises Are Building Agile Talent Models
As we enter January 2026, the traditional corporate "headcount plan" is undergoing a quiet but radical retirement. For decades, the…
In 2024, a mid-sized firm suffered a data breach costing them over $4.6 million. The culprit? The entry point wasn’t a zero-day vulnerability, nor a highly sophisticated phishing campaign. It was an ex-contractor’s cloud access credentials, still active six months after their project had ended.
Poor access governance doesn’t always make headlines, but its consequences are profound. Beyond financial losses, it erodes trust and can lead to regulatory penalties.
In this blog, we’ll trace how seemingly harmless oversights in access governance grow into systemic risks. More importantly, we’ll walk through actionable strategies that help organizations regain visibility, shrink privilege exposure, and build pragmatic access controls that evolve with the business, not against it.
In many organizations, access rights are granted liberally but rarely revoked. Employees change roles, and contractors complete projects, yet their access often remains unchecked. This oversight creates a fertile ground for security breaches.
IBM’s 2025 Cost of a Data Breach Report shows that breaches involving compromised credentials took an average of 292 days to identify and contain, making them among the costliest at $4.45 million globally, and over $10.22 million in the U.S. Such prolonged exposure underscores the dangers of neglected access controls.
Beyond financial losses, these breaches erode stakeholder trust and can lead to regulatory penalties, especially when sensitive data is involved.
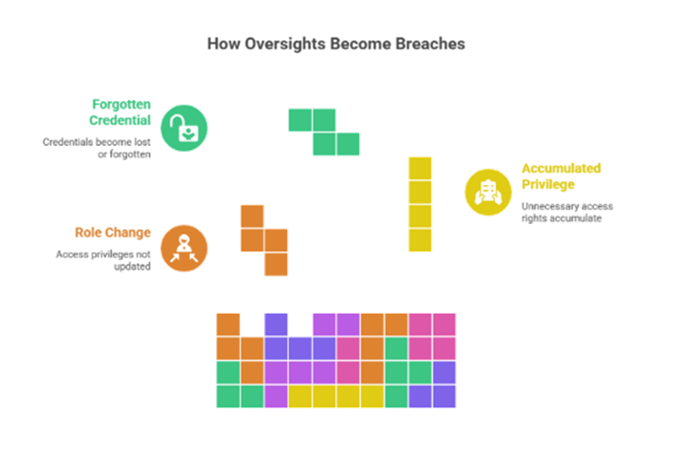
Several recurring issues contribute to poor access governance:
Addressing these issues requires a shift towards more automated and policy-driven access management strategies.
The monetary impact of inadequate access governance is substantial. IBM’s 2025 report indicates that the global average cost of a data breach is now $4.45 million, with U.S. breaches averaging $10.22 million. Credential-related incidents remain among the most expensive, averaging $4.45M globally per event.
These costs encompass detection, response, legal fees, and loss of business. Investing in robust access governance not only mitigates these risks but also proves cost-effective in the long run.
To fortify access controls, organizations should consider the following measures:
By integrating these practices, organizations can significantly reduce the risk of unauthorized access and potential breaches.
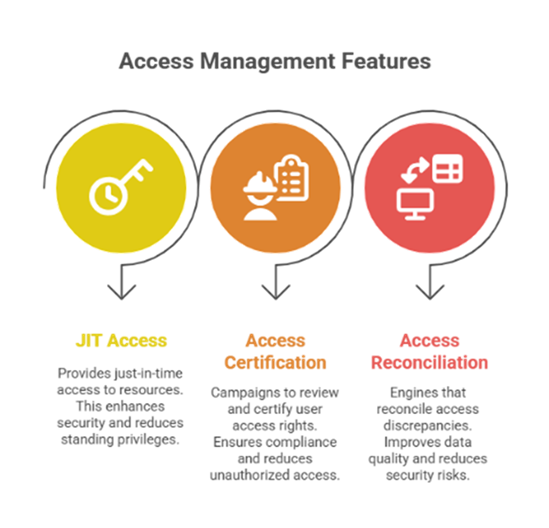
Modern Identity Governance and Administration (IGA) solutions offer advanced features to streamline access management:
Tools like SailPoint and Saviynt have been recognized for their comprehensive identity governance capabilities. Adopting such technologies can enhance security posture and operational efficiency.
Most access governance failures aren’t about who gets in; they’re about who never gets out.
Access is often treated as a one-time event, granted during onboarding, then left untouched indefinitely. But job scopes evolve. Projects end. People leave. What lingers? Access credentials, buried deep within the system, have no business justification for existing.
The solution isn’t more manual reviews; it’s smarter lifecycle logic.
Three models help address this ‘access expiry’ gap:
These aren’t theoretical controls. They’re scalable, auditable, and reduce the likelihood of forgotten credentials, as seen in our introductory example with the ex-contractor.
By treating access as a dynamic asset, with a clear start, purpose, and end, organizations can shrink their privilege footprints without slowing down their workforce.
In 2025, access governance is no longer just operational hygiene; it’s a compliance imperative.
These rules elevate access controls from IT oversight to a board-level obligation. Organizations that fail to get it right now risk fines, liability, and investor skepticism, as well as breach costs.
The repercussions of poor access governance extend beyond immediate financial losses, affecting reputation, compliance, and overall business resilience.
By proactively addressing access management through strategic policies, technological solutions, and cultural shifts, organizations can safeguard their assets and maintain the trust of their stakeholders.
In an era where breaches are increasingly sophisticated and regulations are unforgiving, robust access governance is no longer just a security measure; it’s a business necessity. And with Compunnel’s Cybersecurity Services, enterprises can move beyond reactive cleanup to proactive resilience, aligning access governance with compliance, cost control, and confidence.
