Contingent Workforce Solutions in 2026: How Enterprises Are Building Agile Talent Models
As we enter January 2026, the traditional corporate "headcount plan" is undergoing a quiet but radical retirement. For decades, the…
A surgeon rushes into the OR seconds before an emergency – only to be stopped cold by an “unauthorized access” screen. A traveling nurse, starting her shift, wastes precious minutes guessing credentials before she can view patient charts. In 2025, a HealthTech Research Alliance survey found that 57% of healthcare organizations reported experiencing diagnostic delays due to the fragmentation of access management systems.
In healthcare, delays aren’t only costly but also potentially fatal. Identity and Access Management (IAM) is supposed to bridge the gap between life-saving access and legal disaster. Yet most systems weren’t designed with healthcare’s high stakes in mind. They leave institutions teetering between overprotective barriers and dangerous exposure.
The fallout? Frustrated care teams, over-provisioned access, under-documented audits, and a compliance posture that looks airtight on paper but wobbles under real-world pressure.
This blog unpacks the layers of IAM in healthcare – showing how organizations can sidestep common traps, rethink access models, and modernize security without locking out their frontline caregivers.

In healthcare, time is both a clinical asset and a security liability. Whether it’s a trauma surgeon logging in during a mid-emergency or a nurse reviewing vitals during a shift handover, access must be instantaneous. But many IAM systems prioritize control over urgency.
Poor access design delays treatment, frustrates clinicians, and increases security blind spots. The bigger problem? HIPAA requires accountability, but too many hospitals confuse “tight access” with “right access.”
A recent study by the Healthcare Access Consortium found that 59% of organizations experienced treatment delays due to inefficient identity verification systems. When clinicians are interrupted by login lags or misaligned permissions, it’s not just compliance that suffers; patient outcomes may too.
Most legacy IAM systems were built for 9-to-5 desk jobs, not 24/7 clinical settings.
Healthcare teams rotate shifts, fill in for colleagues, or take on new roles daily. Static models like Role-Based Access Control (RBAC) crumble in dynamic environments. What’s needed is real-time flexibility, not rigid access matrices.
Meanwhile, hospitals are running hybrid stacks: on-prem systems, cloud EHRs, and telemedicine apps. When your IAM can’t unify them, you end up with provisioning delays and inconsistent access.
Key challenges include:
This gap between care and identity control is a growing operational liability.
Hospitals rely heavily on shared workstations, tablets, and carts on wheels. But shared devices come with unshared accountability.
Clinicians sometimes forget to log out, reuse colleague credentials, or leave sessions open during emergencies. While understandable in high-stress contexts, these practices create access shadows – actions taken without proper attribution.
These not only violate HIPAA but also make post-incident forensics nearly impossible.
Practical IAM solutions include:
Modern IAM must account for frontline realities – not just perfect audit trails.
Healthcare IAM walks a tightrope: you must minimize access, but you can’t delay care.
While “least privilege” is foundational, rigid enforcement during emergencies can cost lives. Physicians may need immediate access to data outside their default roles – and they need it now, not after approval queues.
The solution? Context-aware IAM.
It factors in:
Layer in behavioral analytics, and even temporary privilege escalations can be monitored, reversible, and accountable.
Many healthcare organizations see HIPAA as a barrier to efficiency. In truth, it’s a blueprint for intentional design.
HIPAA doesn’t prescribe specific tech – it demands that access be secure, traceable, and justified. If IAM slows clinicians, it’s not HIPAA’s fault – it’s a design flaw.
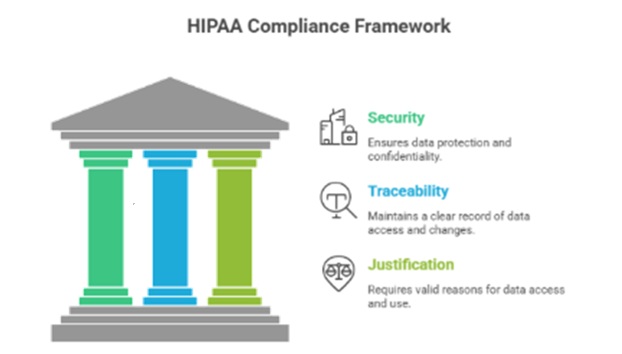
Solutions like Attribute-Based Access Control (ABAC) allow access determined by role and context (location, time, behavior). That gives dynamic control while staying within HIPAA limits.
To maintain compliance without bottlenecks, IAM must:
When done right, compliance becomes a byproduct of smart system design.
IAM in healthcare is evolving from rule-based to context-aware, from reactive to predictive.
In 2025, identity threat detection and response (ITDR) is gaining traction. Organizations are embedding AI to flag anomalous logins and escalate risk dynamically.
Meanwhile, password less authentication (e.g., FIDO passkeys, biometric login) is accelerating adoption – reducing credential fatigue and the attack surface.
The global IAM in healthcare market is projected to grow at a CAGR of ~17.46% from 2025 to 2030.
Invisible IAM is an emerging system that adapts in the background, granting seamless access without user friction – with anomalies escalated automatically.
Imagine:
The goal: reduce authentication friction without weakening oversight.

IAM in healthcare isn’t just a security investment; it’s a patient safety and operational imperative. When systems get in the way, clinicians bypass them. But when systems adapt to care rhythms, security becomes seamless.
The success of IAM won’t be measured by how many requests it blocks HIPAA-compliant, but also by how many it enables safely, truly care-driven, and growth-ready checks. Organizations that shift from control to context, rigidity to responsiveness, will not only remain HIPAA-compliant but also truly care-driven and growth-ready.
